5-21
Cisco ASA Series Firewall CLI Configuration Guide
Chapter 5 NAT Examples and Reference
DNS and NAT
! Use twice NAT to pass traffic between the inside network and the VPN client without
! address translation (identity NAT), w/route-lookup:
nat (outside,inside) source static vpn_local vpn_local destination static inside_nw
inside_nw route-lookup
Troubleshooting NAT and VPN
See the following monitoring tools for troubleshooting NAT issues with VPN:
•
Packet tracer—When used correctly, a packet tracer shows which NAT rules a packet is hitting.
•
show nat detail
—Shows hit counts and untranslated traffic for a given NAT rule.
•
show conn all
—Lets you see active connections including to and from the box traffic.
To familiarize yourself with a non-working configuration vs. a working configuration, you can perform
the following steps:
1.
Configure VPN without identity NAT.
2.
Enter
show nat detail
and
show conn all
.
3.
Add the identity NAT configuration.
4.
Repeat
show nat detail
and
show conn all
.
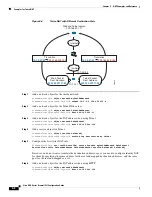
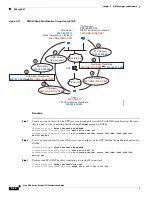
DNS and NAT
You might need to configure the ASA to modify DNS replies by replacing the address in the reply with
an address that matches the NAT configuration. You can configure DNS modification when you
configure each translation rule.
This feature rewrites the address in DNS queries and replies that match a NAT rule (for example, the A
record for IPv4, the AAAA record for IPv6, or the PTR record for reverse DNS queries). For DNS replies
traversing from a mapped interface to any other interface, the record is rewritten from the mapped value
to the real value. Inversely, for DNS replies traversing from any interface to a mapped interface, the
record is rewritten from the real value to the mapped value.
Following are some limitations with DNS rewrite:
•
DNS rewrite is not applicable for PAT because multiple PAT rules are applicable for each A-record,
and the PAT rule to use is ambiguous.
•
If you configure a twice NAT rule, you cannot configure DNS modification if you specify the source
address as well as the destination address. These kinds of rules can potentially have a different
translation for a single address when going to A vs. B. Therefore, the ASA cannot accurately match
the IP address inside the DNS reply to the correct twice NAT rule; the DNS reply does not contain
information about which source/destination address combination was in the packet that prompted
the DNS request.
•
DNS rewrite requires DNS application inspection to be enabled, which it is on by default. See
for more information.
•
DNS rewrite is actually done on the xlate entry, not the NAT rule. Thus, if there is no xlate for a
dynamic rule, rewrite cannot be done correctly. The same problem does not occur for static NAT.
Содержание ASA 5512-X
Страница 5: ...P A R T 1 Service Policies and Access Control ...
Страница 6: ......
Страница 50: ...3 14 Cisco ASA Series Firewall CLI Configuration Guide Chapter 3 Access Rules History for Access Rules ...
Страница 51: ...P A R T 2 Network Address Translation ...
Страница 52: ......
Страница 126: ...5 28 Cisco ASA Series Firewall CLI Configuration Guide Chapter 5 NAT Examples and Reference DNS and NAT ...
Страница 127: ...P A R T 3 Application Inspection ...
Страница 128: ......
Страница 255: ...P A R T 4 Connection Settings and Quality of Service ...
Страница 256: ......
Страница 288: ...12 14 Cisco ASA Series Firewall CLI Configuration Guide Chapter 12 Quality of Service History for QoS ...
Страница 303: ...P A R T 5 Advanced Network Protection ...
Страница 304: ......
Страница 339: ...P A R T 6 ASA Modules ...
Страница 340: ......
Страница 398: ...17 28 Cisco ASA Series Firewall CLI Configuration Guide Chapter 17 ASA CX Module History for the ASA CX Module ...