Page 160 SonicWALL SonicOS Standard Administrator’s Guide
The IP address of the machine under attack and the source of the attack is displayed. In most attacks,
the source address shown is fake and does not reflect the real source of the attack.
Tip!
Some network conditions can produce network traffic that appears to be an attack, even if no one is
deliberately attacking the LAN. Verify the log messages with SonicWALL Tech Support before
contacting your ISP to determine the source of the attack.
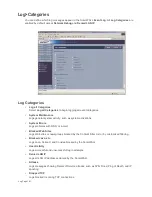
Log Table
The log is displayed in a table and is sortable by column. The log table columns include:
•
Time - the date and time of the event.
•
Message - provides description of the event.
•
Source - displays source network and IP address.
•
Destination - displays the destination network and IP address.
•
Notes - provides additional information about the event.
•
Rule - notes Network Access Rule affected by event.
Refresh
Clicking the Refresh button updates Log events.
Clear Log
Clicking Clear Log deletes the contents of the log.
E-mail Log
If you have configured the SonicWALL to e-mail log files, clicking E-mail Log sends the current log files
to the e-mail address specified in the Log>Automation>E-mail section.
Note:
The SonicWALL can alert you of important events, such as an attack to the SonicWALL. Alerts are
immediately sent via e-mail, either to an e-mail address or to an e-mail pager. For sending alerts, you
must enter your e-mail address and server information in the Log>Automation page.
Summary of Contents for SonicOS Enhanced 2.2
Page 19: ...Page 6 SonicWALL SonicOS Standard Administrator s Guide...
Page 45: ...Page 32 SonicWALL SonicOS Standard Administrator s Guide...
Page 65: ...Page 52 SonicWALL SonicOS Standard Administrator s Guide...
Page 141: ...Page 128 SonicWALL SonicOS Standard Administrator s Guide...
Page 185: ...Page 172 SonicWALL SonicOS Standard Administrator s Guide...
Page 188: ...Page 175...
Page 189: ...Page 176 SonicWALL SonicOS Enhanced Administrator s Guide...