VPN Page 115
Configuring a VPN Policy with IKE using a Third Party Certificate
Alert!
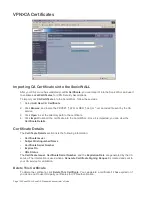
You must have a valid certificate from a third party Certificate Authority installed on your SonicWALL
before you can configure your VPN policy with IKE using a third party certificate.
To create a VPN SA using IKE and third party certificates, follow these steps:
1.
In the VPN>Settings page, click Add. The VPN Policy window is displayed.
2.
In General tab, select IKE using 3rd Party Certificates.
3.
Type a Name for the Security Association in the Name field.
4.
Type the IP address or Fully Qualified Domain Name (FQDN) of the primary remote SonicWALL in
the IPSec Primary Gateway Name or Address field. If you have a secondary remote SonicWALL,
enter the IP address or Fully Qualified Domain Name (FQDN) in the IPSec Secondary Gateway
Name or Address field.
5.
Select a certificate from the Third Party Certificate menu.
6.
Select Distinguished name, E-Mail ID, or Domain name from the Peer Certificate’s ID Type menu.
7.
Type an ID string in the ID string to match field.
8.
Click on the Network tab.
9.
Under Local Networks, select a local network from Choose local network from list if a specific local
network can access the VPN tunnel. If hosts on this side of the VPN connection will be obtaining their
addressing from a DHCP server on the remote side of the tunnel, select Local network obtains IP
addresses using DHCP through this VPN tunnel. If traffic can originate from any local network,
select Any Address.
10. Under Destination Networks, select Use this VPN Tunnel as default route for all Internet traffic
if all remote VPN connections access the Internet through this SA. You can only configure one SA to
use this setting. If the remote side of this VPN connection is be obtaining its addressing from a DHCP
server on this side of the tunnel, select Destination network obtains IP addresses using DHCP
server through this tunnel. Alternatively, select Choose Destination network from list, and select
the address object or group.
11. Click the Proposals tab.
12. In the IKE (Phase 1) Proposal section, select the following settings:
Select Aggressive Mode from the Exchange menu.
Select Group 2 from the DH Group menu.
Select 3DES from the Encryption menu.
Enter a maximum time in seconds allowed before forcing the policy to renegotiate and exchange keys
in the Life Time field. The default settings is 28800 seconds (8 hours).
13. In the Ipsec (Phase 2) Proposal section, select the following settings:
Select ESP from the Protocol menu.
Select 3DES from the Encryption menu.
Select SHA1 from the Authentication menu.
Select Enable Perfect Forward Secrecy if you want an additional Diffie-Hellman key exchange as
an added layer of security, then select Group 2 from the DH Group menu.
Enter a maximum time in seconds allowed before forcing the policy to renegotiate and exchange keys
in the Life Time field. The default settings is 28800 seconds (8 hours).
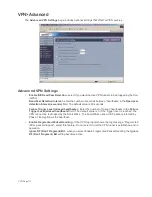
14. Click the Advanced tab. Select any optional configuration options you want to apply to your VPN
policy in the Advanced Settings section.
Summary of Contents for SonicOS Enhanced 2.2
Page 19: ...Page 6 SonicWALL SonicOS Standard Administrator s Guide...
Page 45: ...Page 32 SonicWALL SonicOS Standard Administrator s Guide...
Page 65: ...Page 52 SonicWALL SonicOS Standard Administrator s Guide...
Page 141: ...Page 128 SonicWALL SonicOS Standard Administrator s Guide...
Page 185: ...Page 172 SonicWALL SonicOS Standard Administrator s Guide...
Page 188: ...Page 175...
Page 189: ...Page 176 SonicWALL SonicOS Enhanced Administrator s Guide...