POWERED BY
FLUIDIGM
LAN
AC 100–240V
50–60Hz, 8A
US
BU
SB
HDMI
COMPRESSION AIR INLET
(OPTIONAL)
70–90 PSI ONLY
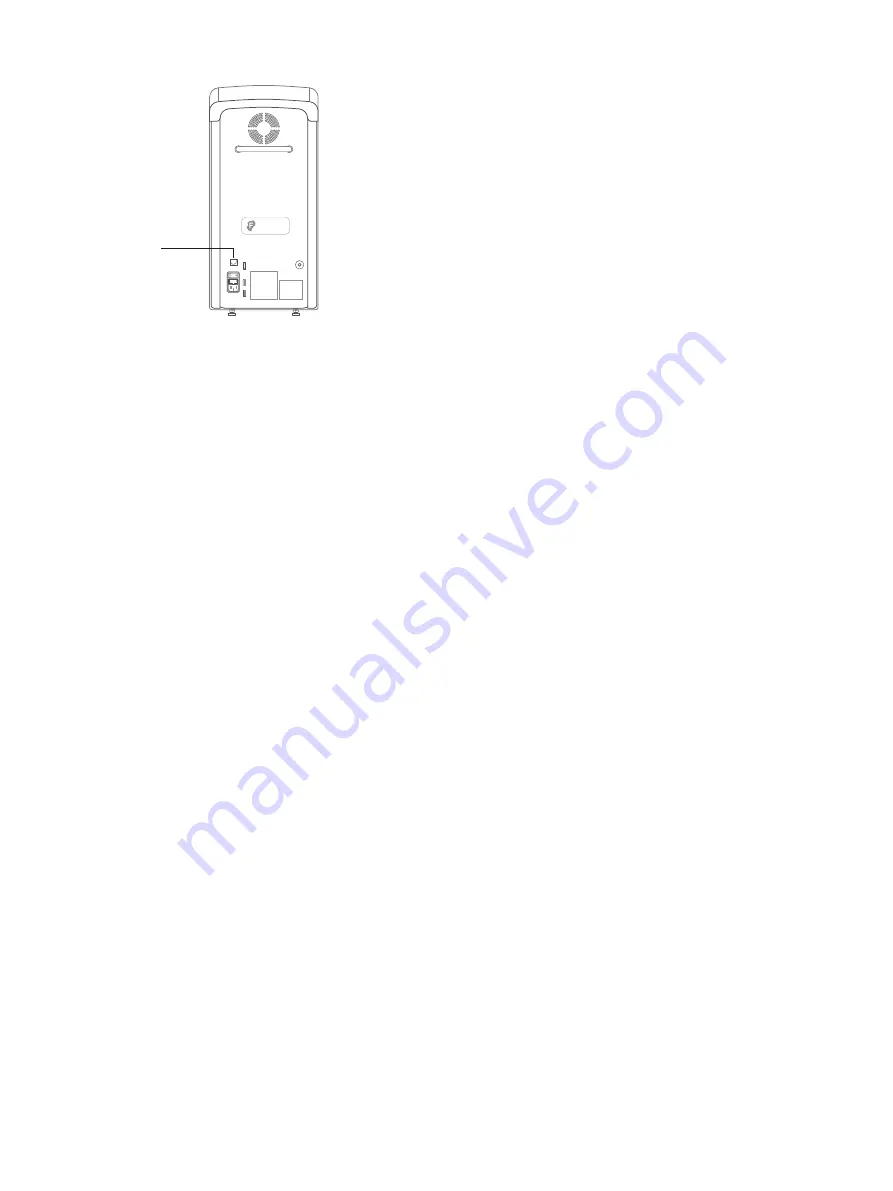
Ethernet port
Figure 5. Ethernet port
2.7.1 Network Requirements
When adding Signature Q100 to network, it is necessary to add it to a secured segmented network that cannot access
internet. Olink will not take any responsibilities for the risks associated with networking of the instrument.
To connect the Signature Instrument to the network the following requirements must be met:
• A DHCP enabled network with a dynamic IP-address allocation.
• The Instrument must be prevented from reaching the Internet. (See Network Segmentation)
• Communication attempts to the Instrument must allow TCP port: 8085
2.7.2 Network Segmentation
2.7.2.1 Introduction
To handle any security issues in the Local Network and making sure that the risk to the connected equipment is as small as
possible Network Segmentation is an important key factor. By segmenting the network, the following advantages can be
reached:
• Damage control and limitation in case of an incident via the smaller attack surface. A smaller subset of network devices
is within the same scope.
• Improved access control for external and internal network security.
–
In this specific case the Signature Instrument should not reach the Internet and receive updates or be exposed to
threats.
• Reducing the attack plane and scope of compliance requirements related auditing
• Improved performance with less congestion on network traffic
• Better analytics around network monitoring, network access and network devices
• Endpoint device protection, especially important as IoT devices become more common
Network segmentation can boost your overall security policy by limiting access privileges to those who need it, protecting
the network from widespread cyberattacks and enabling better network performance by reducing the number of users in
specific zones.
2.7.2.2 How to implement Network Segmentation
This is heavily dependent on the flavor of Network Equipment used, and how to specifically implement segmentation can
only be answered when this is known. There are, however, a few basic technologies that is common for most solutions.
8









































