Chapter 4. Security
This chapter provides information about how to protect your computer from theft and unauthorized use.
Security features
The following security features are available on your computer:
• Cover presence switch (also called intrusion switch) (only available on some models)
The cover presence switch prevents your computer from logging in to the operating system when the
computer cover is not properly installed or closed. To enable the cover presence switch connector
on the system board, to the following:
1. Start the Setup Utility program. See “Starting the Setup Utility program” on page 77.
2. Set the Administrator Password. See “Setting, changing, and deleting a password” on page 78.
3. From the
Security
submenu, select
Chassis Intrusion Detection
➙
Enabled
. The cover presence
switch connector on the system board is enabled.
When the cover presence switch detects that your computer cover is not properly installed or closed
when you turn on the computer, an error message will be displayed. To bypass the error message and
log in to the operating system, do the following:
1. Properly install or close your computer cover. See “Completing the parts replacement” on page 66.
2. Press F1 to enter the Setup Utility program. Then press F10 to save and exit the Setup Utility
program. The error message will not be displayed again.
• Ability to enable and disable devices and USB connectors
For more information, see “Enabling or disabling a device” on page 79.
• Startup sequence control
For more information, see “Selecting or changing the startup device sequence” on page 80.
• Startup without keyboard or mouse
Your computer is able to log in to the operating system without keyboard or mouse connected.
• Trusted Platform Module (TPM)
Trusted Platform Module is a secure cryptoprocessor that can store cryptographic keys that protect
information stored in your computer.
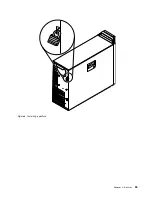
Locking the computer cover
Locking the computer cover helps prevent unauthorized people from gaining access to the inside of your
computer. A keylock
1
comes with this product built into the computer cover. The keys
2
for the cover
are attached to the rear of the machine. For security, store the keys in a secure place when you are not
using them.
© Copyright Lenovo 2012, 2014
31
Summary of Contents for ThinkStation D30
Page 1: ...ThinkStation D30 User Guide Machine Types 4353 and 4354 ...
Page 6: ...iv ThinkStation D30 User Guide ...
Page 12: ...x ThinkStation D30 User Guide ...
Page 28: ...16 ThinkStation D30 User Guide ...
Page 45: ...Figure 8 Installing a padlock Chapter 4 Security 33 ...
Page 48: ...36 ThinkStation D30 User Guide ...
Page 80: ...68 ThinkStation D30 User Guide ...
Page 94: ...82 ThinkStation D30 User Guide ...
Page 104: ...92 ThinkStation D30 User Guide ...
Page 130: ...118 ThinkStation D30 User Guide ...
Page 138: ...126 ThinkStation D30 User Guide ...
Page 142: ...130 ThinkStation D30 User Guide ...
Page 146: ...134 ThinkStation D30 User Guide ...
Page 150: ...138 ThinkStation D30 User Guide ...
Page 151: ......
Page 152: ......