Chapter 5 Wireless
B222s User’s Guide
50
5.2.4 WPA(2) Authentication
The WPA2 security mode is currently the most robust form of encryption for wireless networks. It
requires a RADIUS server to authenticate user credentials and is a full implementation the security
protocol. Use this security option for maximum protection of your network. However, it is the least
backwards compatible with older devices.
The WPA security mode is a security subset of WPA2. It requires the presence of a RADIUS server
on your network in order to validate user credentials. This encryption standard is slightly older than
WPA2 and therefore is more compatible with older devices.
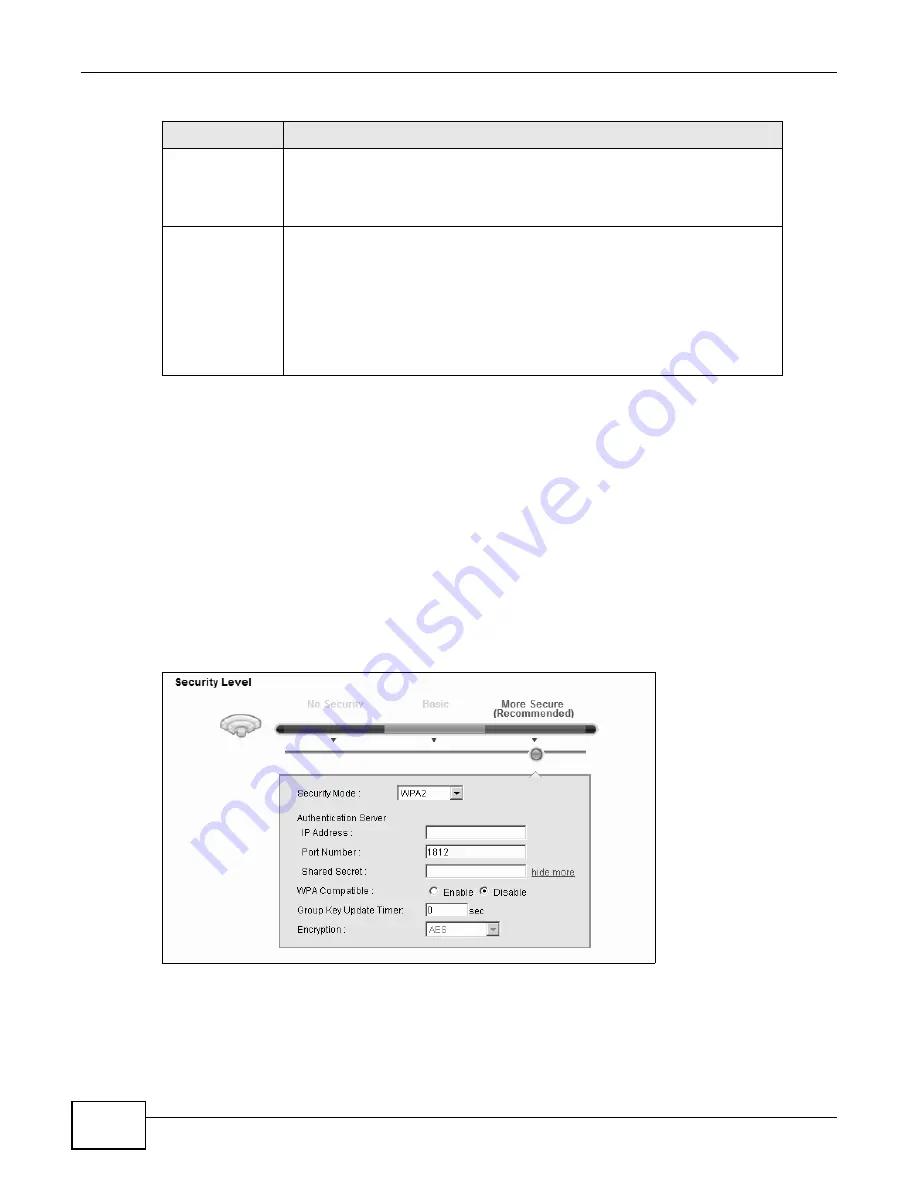
Click Network Settings > Wireless to display the General screen. Select More Secure as the
security level. Then select WPA or WPA2 from the Security Mode list.
Figure 24
Wireless > General: More Secure: WPA(2)
WPA-PSK
Compatible
This field appears when you choose WPA-PSK2 as the Security Mode.
Check this field to allow wireless devices using WPA-PSK security mode to
connect to your LTE Device. The LTE Device supports WPA-PSK and WPA2-PSK
simultaneously.
Encryption
If the security mode is WPA-PSK, the encryption mode is set to TKIP to enable
Temporal Key Integrity Protocol (TKIP) security on your wireless network.
If the security mode is WPA-PSK2 and WPA-PSK Compatible is disabled, the
encryption mode is set to AES to enable Advanced Encryption System (AES)
security on your wireless network. AES provides superior security to TKIP.
If the security mode is WPA-PSK2 and WPA-PSK Compatible is enabled, the
encryption mode is set to TKIPAES MIX to allow both TKIP and AES types of
security in your wireless network.
Table 10
Wireless > General: WPA(2)-PSK (continued)
LABEL
DESCRIPTION
Summary of Contents for B222s
Page 4: ...Contents Overview B222s User s Guide 4 ...
Page 12: ...Table of Contents B222s User s Guide 12 ...
Page 13: ...13 PART I User s Guide ...
Page 14: ...14 ...
Page 28: ...28 ...
Page 78: ...Chapter 7 Routing B222s User s Guide 78 ...
Page 82: ...Chapter 8 DNS Route B222s User s Guide 82 ...
Page 102: ...Chapter 10 Network Address Translation NAT B222s User s Guide 102 ...
Page 114: ...Chapter 12 Firewall B222s User s Guide 114 ...
Page 120: ...Chapter 14 Parental Control B222s User s Guide 120 ...
Page 125: ...Chapter 15 VoIP B222s User s Guide 125 ...
Page 144: ...Chapter 15 VoIP B222s User s Guide 144 ...
Page 154: ...Chapter 17 Traffic Status B222s User s Guide 154 ...
Page 156: ...Chapter 18 User Account B222s User s Guide 156 ...
Page 170: ...Chapter 24 Backup Restore B222s User s Guide 170 ...
Page 172: ...Chapter 25 Diagnostic B222s User s Guide 172 ...
Page 218: ...Appendix B Setting Up Your Computer s IP Address B222s User s Guide 218 ...
Page 228: ...Appendix C Pop up Windows JavaScript and Java Permissions B222s User s Guide 228 ...
Page 252: ...Appendix E Common Services B222s User s Guide 252 ...






























