Certificate Management
Functions
EDS500
Cerficate
external
Cerficate
signing request
EC key
device
EC key
external
Key
PEM format
upload
Cerficate
device / self-signed
Browser
download
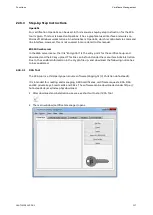
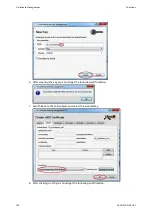
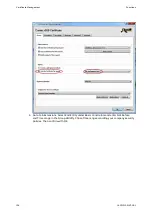
b) Use external EC key and self-signed funcon of device.
EC key
device
Cerficate
device / Self-signed
EDS500
Browser
download
a) Use default key and self-signed cerficate of device
Figure 35: Device key (a) or external key (b) with self-signed certificates
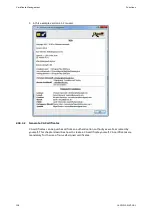
The certificates generated in this way are device-specific. This means that this certificate
is only valid for this device and not for other EDS500 managed switches. If several EDS500
managed switches are used, all certificates must be downloaded from the devices and
integrated into the browser.
The trust in self-signed certificates is legitimated by the fact that they are signed directly by
the device. However, for several reasons it may be necessary to use CA-signed certificates
(e.g. security guideline, handling ...).
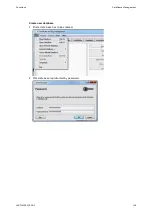
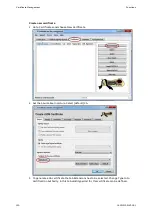
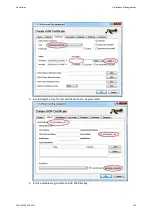
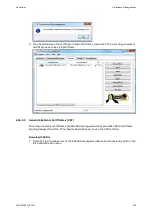
External certificates can be created in two ways: Via a certificate signig request (CSR) or
via an external program (via external program only, if private key exists externally). In the
case of the CSR method, a .csr file is downloaded from the device. This file is signed with a
CA and results in a device-specific .crt file. This .crt file is the actual certificate and have to
be uploaded to the device. It replaces the device certificate. In the case of the usage of an
external program a .crt file can directly be generated from the EC key and a CA.
External certificates have the advantage that they not only trust themselves, they additionaly
trust all higher-level certificates (e.g. CA certificates). That gives you the possibility to
esteblish a HTTPS connection to all EDS500 managed switches in a network with just one
high-level certificate. The circumstance of integrating each individual certificate from all
devices into the browser is eliminated.
114
1KGT151021
V000 1
Содержание EDS500 Series
Страница 8: ...References Introduction 8 1KGT151021 V000 1 ...
Страница 152: ...Certificate Management Functions 152 1KGT151021 V000 1 ...
Страница 155: ...1KGT151021 V000 1 155 ...