Functions
Cryphographic Key
ADVICE
Devices that have been shipped with a software version without SSH support (SWOPS <
1.33.0), have no individual cryptographic key but use a standard value as key. An individual
key has to be applied for security reasons when cryptographic protocols are used. Such
devices can be detected during boot or login or by the output of the command <show
system ssh> at the message
Warning: SSH server is using the default host key.
ADVICE
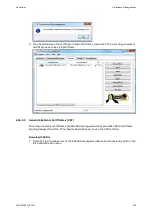
In order to establish encrypted connections so-called crypto sessions get pre-calculated to
reduce the time for establishing a connection. If there are no crypto sessions in the device
then encrypted connections can only be established after at least one crypto session has
been calculated. This status can be monitored with an alarm with the commands <set
system ssh alarm-if-notready> and <set system ssh warn-if-notready>.
2.35.2
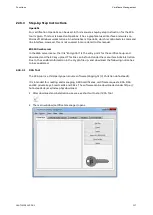
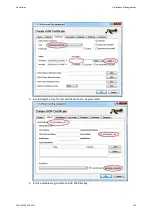
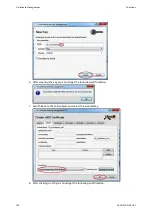
Generate and Apply Cryptographic Key
The program PuTTYgen can be used to create a cryptographic key. PuTTYgen is part of the
Open Source Terminal Emulator Suite PuTTY and can be obtained from the project homepage
http://www.chiark.greenend.org.uk/~sgtatham/putty/. The file can be executed directly
without installation.
A graphical user interface is shown when starting PuTTYgen to generate the key.
1KGT151021
V000 1
109
Содержание EDS500 Series
Страница 8: ...References Introduction 8 1KGT151021 V000 1 ...
Страница 152: ...Certificate Management Functions 152 1KGT151021 V000 1 ...
Страница 155: ...1KGT151021 V000 1 155 ...