52
User
Manual
GWG Gateway
tunnel. Select the type you want to use: IP or Subnet. NOTE: The Local Security
Group Type you select should match the Remote Security Group Type selected on
the IPSec device at the other end of the tunnel.
Subnet Mask
Enter the subnet mask.
Remote Security
Gateway Type
Select the type you want to use: IP Only - Only a specific IP address will be able to
establish a tunnel. NOTE: The Remote Security Gateway Type you select should
match the Local Security Gateway Type selected on the IPSec device at the other
end of the tunnel.
IP Address
IP address of the remote end with which the tunnel will be formed.
Remote ID Type
Authentication identity for one of the participant. Can be an IP address or fully–
qualified domain name preceded by @.
Remote Security Group
Type
Define if only the computer with a specific IP address or whole subnet will be able
to access the tunnel.
IP Address
Select the remote LAN user(s) behind the Geneko Router at the other end that can
use this IPSec tunnel. Select the type you want to use: IP or Subnet. NOTE: The
Remote Security Group Type you select should match the Local Security Group
Type selected on the IPSec device at the other end of the tunnel.
Subnet Mask
Enter the subnet mask.
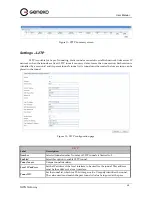
IPSec Setup
In order to establish an encrypted tunnel, the two ends of an IPSec tunnel must
agree on the methods of encryption, decryption and authentication. This is done by
sharing a key for the encryption code. For key management, the Geneko Router
uses only IKE with Preshared Key mode.
Key Exchange mode
IKE with Preshared Key
IKE is an Internet Key Exchange protocol used to negotiate key material for Security
Association (SA). IKE uses the Preshared Key to authenticate the remote IKE peer.
Both ends of IPSec tunnel must use the same mode of key management and the
same key.
IKE with Preshared Key File
One or more files which contain preshared secret must be uploaded in the IPSec key
file management menu.
IMPORTANT
: context of the file should be plain text and
without space characters, so if a tool for generating secrets such as OpenSSL,
OpenVPN or IPSec PKI commands were used, make sure there are no spaces for
example like in term "----BEGIN CERTIFICATE----", where there is a space between
words BEGIN and CERTIFICATE.
IKE with X509 certificates and PSK
This option is used when X509 certificates are used for authentication. Certificate
files must first be uploaded through pages which are in the main menu under file
management. Pre shared key (PSK) is entered manually and must match on both
peers.
IKE with X509 certificates and PSK file
This option is used when X509 certificates are used for authentication. Certificate
files must first be uploaded through pages which are in the main menu under file
management. Pre shared key file (PSK) is chosen from uploaded PSK files in the
IPSec key file management and must match on both peers.
Mode
Mode of IPSec can be main or aggressive.
Summary of Contents for GWG
Page 1: ...GWG Gateway USER MANUAL GWG Document version 1 0 1 Date July 2016 WWW GENEKO RS ...
Page 43: ...43 User Manual GWG Gateway Figure 22 RIP configuration page ...
Page 136: ...136 User Manual GWG Gateway Click OK Figure 125 Policies from trust to untrust zone ...
Page 156: ...156 User Manual GWG Gateway Figure 150 Configuration page for SIM keepalive ...