Book Title
Ridgeline Concepts and Solutions Guide
336
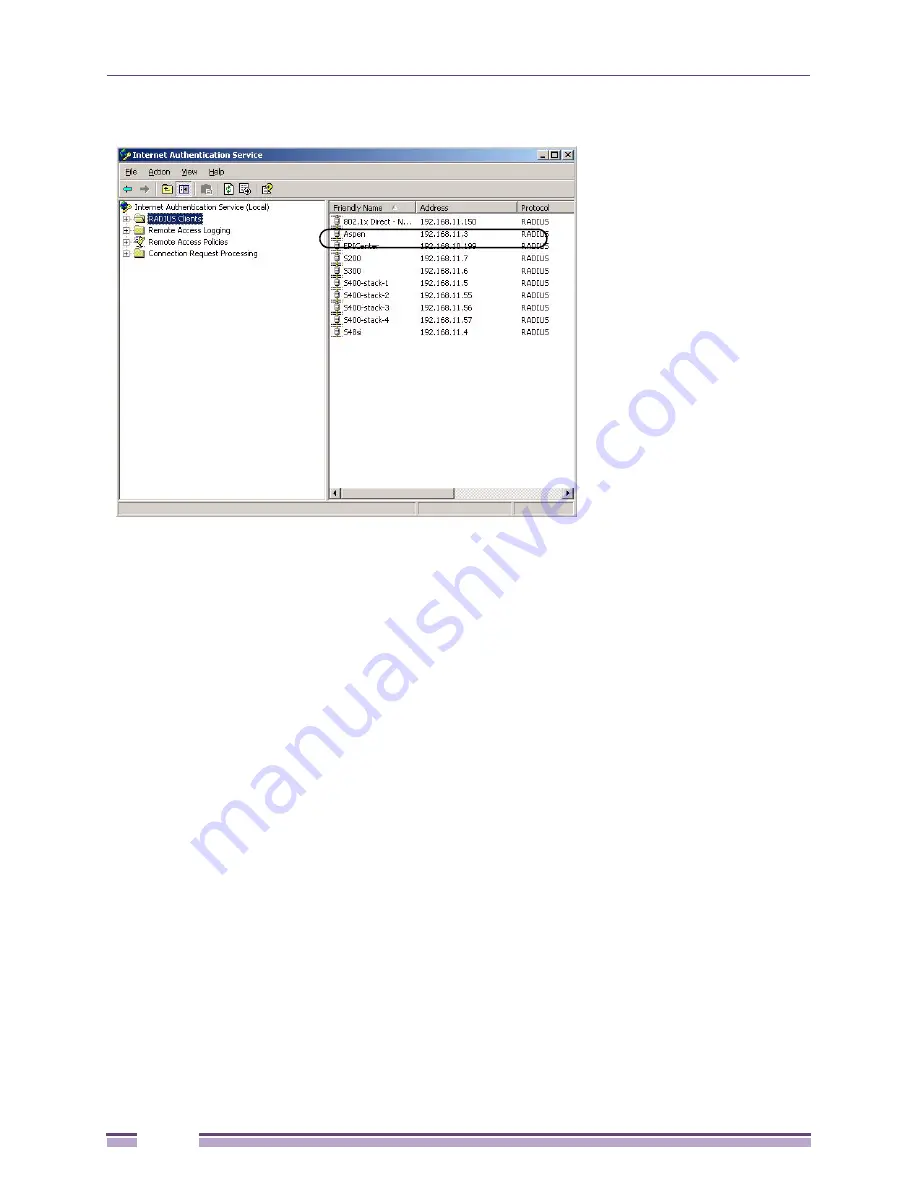
Figure 277: Verify the RADIUS client in IAS
Step 4. Create a Remote Access Policy for Ridgeline
Users
Create a Microsoft Internet Authentication Remote Access Policy for each type of Ridgeline role that
you plan to use within Ridgeline. For each different role (predefined roles such as Admin or Manager,
or user-defined roles) a Remote Access Policy is needed, configured with the role information that must
be transmitted to Ridgeline along with the user’s authentication status.
To create a Remote Access Policy:
1
Under the Internet Authentication Service, right click the Remote Access Policies folder, select
New
and then
Remote Access Policy
.
The
New Remote Access Policy Wizard
will start. Click
New
to continue.
2
Type type a name for the Policy Name (see
Figure 278
, where
Ridgeline
is used as an example), then
click
Next
.
If you need to create multiple policies, each must have a unique name, such as
NMS-Admin
and
NMS-Monitor
.
Summary of Contents for Ridgeline 3.0
Page 14: ...Related Publications Ridgeline Concepts and Solutions Guide 12 ...
Page 26: ...Ridgeline Overview Ridgeline Concepts and Solutions Guide 24 ...
Page 52: ...Getting Started with Ridgeline Ridgeline Concepts and Solutions Guide 50 ...
Page 78: ...Using Map Views Ridgeline Concepts and Solutions Guide 76 ...
Page 88: ...Provisioning Network Resources Ridgeline Concepts and Solutions Guide 86 ...
Page 103: ...6 Ridgeline Concepts and Solutions Guide 101 Figure 63 E Line Service Details Window ...
Page 104: ...Managing Ethernet Services Ridgeline Concepts and Solutions Guide 102 ...
Page 114: ...Importing Services Ridgeline Concepts and Solutions Guide 112 ...
Page 132: ...Managing and Monitoring VPLS Domains Ridgeline Concepts and Solutions Guide 130 ...
Page 146: ...Managing VLANs Ridgeline Concepts and Solutions Guide 144 ...
Page 190: ...Managing Your EAPS Configuration Ridgeline Concepts and Solutions Guide 188 ...
Page 202: ...Managing Network Security Ridgeline Concepts and Solutions Guide 200 ...
Page 350: ...Book Title Ridgeline Concepts and Solutions Guide 348 ...
Page 372: ...Book Title Ridgeline Concepts and Solutions Guide 370 ...