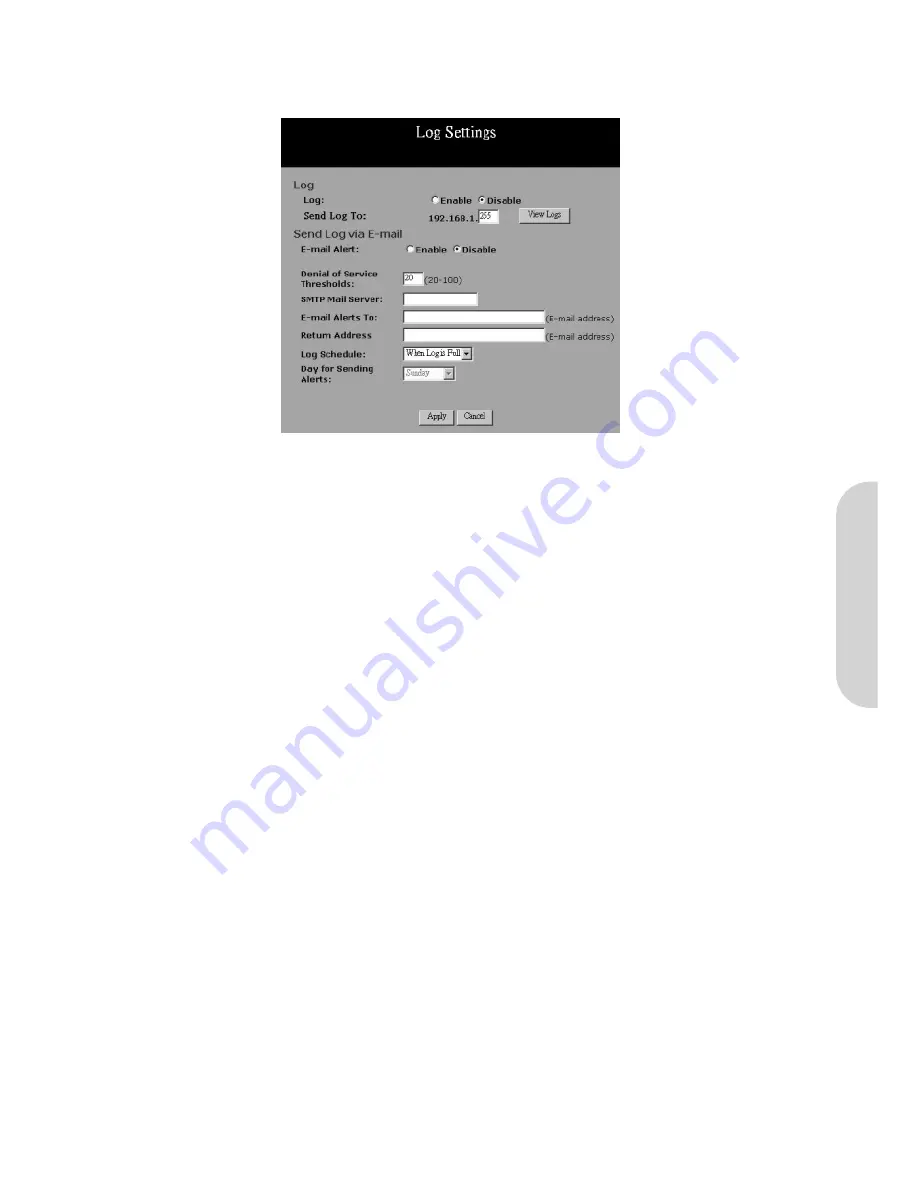
5-3 Log
The Log application provides the administrator with the ability to trace internet connection. With viewing the Log information, an administrator can send the record to
specific LAN PCs to have the real time monitor.
Figure 44. Log Settings
Access Log:
Check the “
Enable
” option if you want to activate this function.
Send Log:
Enter the IP address of the PC that you wish to use to view the Log information.
View Log:
Click this button to view the log on-line.
Send Log via E-mail:
The Firewall log can be sent via e-mail.
Denial of Service Thresholds:
The threshold is used to determine whether the attempt of establishing connection is a DoS attack.
SMTP Mail Server:
The domain name of the IP Address of your ISP’s outgoing e-mail server. You may find this information when you apply for e-mail service from
your ISP.
E-mail Alert to:
Enter the e-mail address you wish to send to.
Return Address:
Enter the e-mail address you wish to send to if the alert e-mail cannot be sent to the address above.
Log Schedule:
Select from the drop down list when you wish the alert e-mail to be sent.
When Log is Full:
The alert e-mail will be sent when log space is full. This is typically when there are about 30 entries.
Hourly:
The alert e-mail will be sent each hour.
Daily:
The alert e-mail will be sent each day at midnight.
Weekly:
The alert e-mail will be sent each week.
Day of Sending Alert:
When “Weekly” is selected as Log Schedule, you can select which day in a week to send the alert e-mail.
Click the “
Apply
” button after making any changes, or click the “
Cancel
” button to exit the screen without saving any changes.
ENGLISH
26



























