11
2.
IP Address:
Selecting this item allows only the specific PC with the IP address you enter in the IP field to the Tunnel.
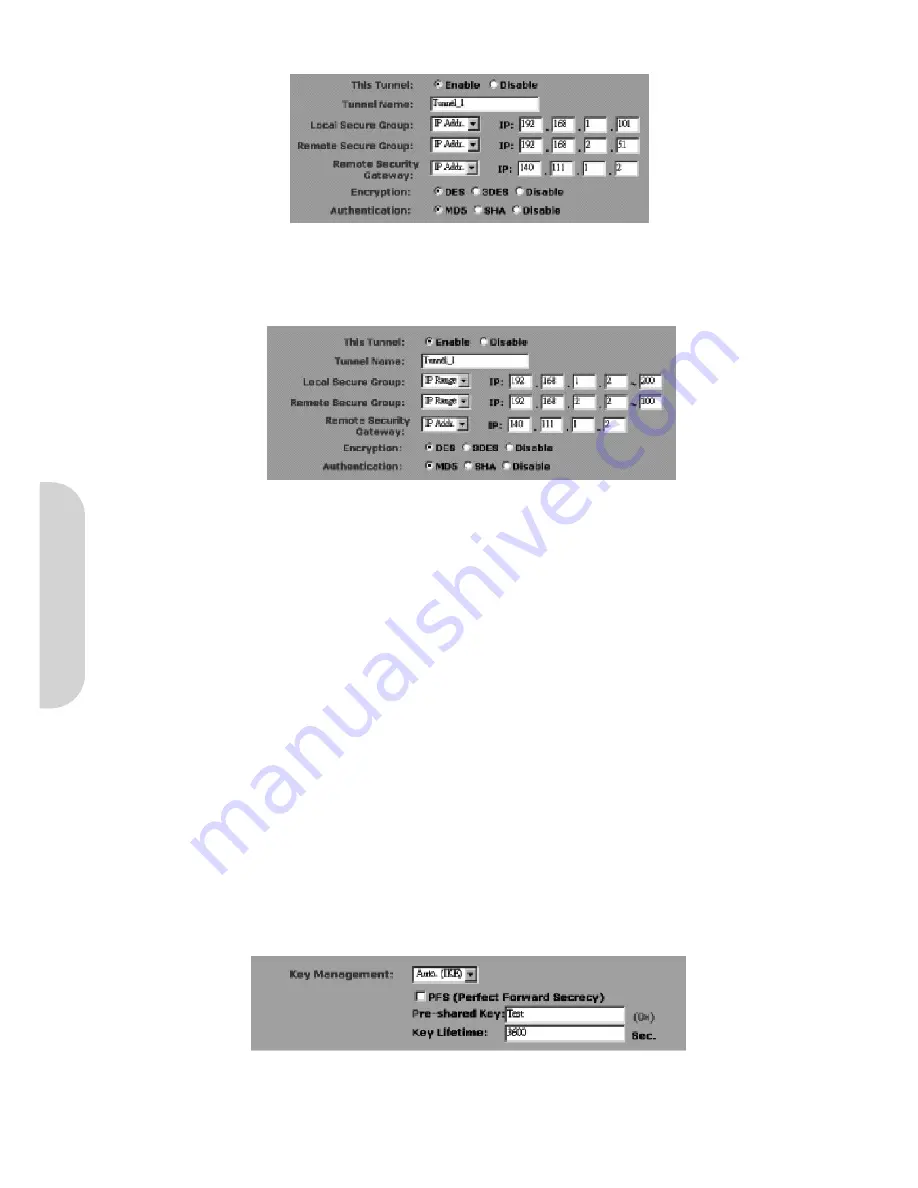
Figure 17. Restricting IP Access
Refer to the above figure as an example. Only the PC with IP Address 192.168.1.101 will have the access from the local side of Tunnel. Similarly, only the PC with IP
Address 192.168.2.51 can access the Tunnel from the other end.
3.
IP Range:
Selecting this item allows a specific group of PCs access to theTunnel.
Figure 18. Multiple IP Access
Refer to the above figure as an example. Only the PCs with the IP addresses between 192.168.1.2 and 192.168.1.200 can access the local side of the Tunnel.
Similarly, PCs with IP Address between 192.168.2.2 and 192.168.2.100 can access the Tunnel from the other end.
4.
Host:
If you select “Host”, the value set here should be the same as the Remote Security Gateway setting.
5.
Any:
When this option is selected, the router accepts remote requests from any IP address, such as mobile users or telecommunications device using dynamic IP
address. Note that the router cannot initial VPN connection when “Any” is selected as Remote Security Group,
•
Remote Security Gateway:
Defines the end point of VPN Tunnel at the other side of the internet. The remote VPN Tunnel end point can be either a:
-
VPN Router,
-
VPN Server,
-
Host with VPN software.
For example, if the VPN device at the other end of the Tunnel is a VPN router, enter the WAN IP Address of that VPN router in this section. For more detail, refer to the
description of “
Example - establish the VPN connection
” on the next few pages.
IP Address:
Use IP Address to identify the remote VPN Tunnel end point.
FQDN:
Use domain name to identify the remote VPN Tunnel end point.
Any:
Accepts remote requests from any IP address. Note that the router cannot initial VPN connection when “Any” is selected.
•
Encryption:
This gives the VPN connection added security. There are two different types of encryption: “
DES
” or “
3DES
”. Both ends of the Tunnel must use the
same encryption type
. You may also choose to disable encryption by selecting “
Disable
”.
•
Authentication:
This item adds another level of security. There are two types of authentication: “
MD5
” and “
SHA
”. Both ends of the Tunnel must use the same
authentication type
. You may also choose to disable authentication by selecting “
Disable
”.
•
Key Management:
For encryption to work, both ends of the Tunnel need to know the encryption key. By using the
Key Management
drop down list, you can
choose two of two methods to set the Encryption Key: “
key
”:
Auto (IKE)
or
Manual
. Both ends of the Tunnel must use the
key management
.
Figure 19. Key Management
With
Auto (IKE)
, users must enter a series of characters in the “
Pre-shared Key
” field. In the example shown in the figure above, the word
Test
has been used.
The program will automatically generate the correct codes to be used in the encryption and authentication based on the word you entered. You may use any
combination of up to 23 alphanumeric characters in this field. No special characters or spaces are allowed.
ENGLISH




























