Billion 810VGTX Router
Page | 92
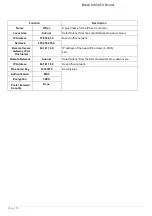
Username: If you are a Dial-Out user (client), enter the username provided to you by your Host. If you are a Dial-In user
(server), enter your own username.
Password: If you are a Dial-Out user (client), enter the password provided to you by your Host. If you are a Dial-In user
(server), enter your own password.
Authentication Type: Default is Auto if you want the router to determine the authentication type to use, or else manually
specify CHAP (Challenge Handshake Authentication Protocol) or PAP (Password Authentication Protocol) if you know
which type the server is using (when acting as a client), or else the authentication type you want clients connecting to
you to use (when acting as a server). When using PAP, the password is sent unencrypted, whilst CHAP encrypts the
password before sending, and also allows for challenges at different periods to ensure that the client has not been
replaced by an intruder.
Tunnel Authentication: This enables the router to authenticate both the L2TP remote and L2TP host systems. This is
only valid when L2TP the remote system supports this feature.
Secret: The secure password length should be 16 characters which may include numbers and characters.
Active as default route: Commonly used by the Dial-out connection. All packets will route through the VPN tunnel to the
Internet; therefore, activating the function may degrade Internet performance.
Remote Host Name (Optional Enter the hostname of the remote VPN device. It is a tunnel identifier to check if the
Remote VPN device matches with the Remote hostname provided. If the remote hostnames match, the tunnel will be
connected; otherwise, it will be dropped.
Caution: This only applies when the router is acting as a VPN server. This option should be used by advanced
users only.
Local Host Name (Optional): Enter hostname of Local VPN device that is connected / established a VPN tunnel. By
default, the router’s default hostname is
home.gateway
.
IPSec: Enable to enhance your L2TP VPN security.
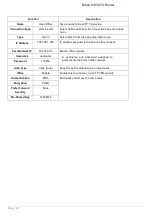
Authentication: Authentication establishes the integrity of the datagram and ensures that it is not tampered with during
transmission. There are three options, Message Digest 5 (MD5), Secure Hash Algorithm (SHA1) or NONE. SHA1 is
more resistant to brute-force attacks than MD5, however it is slower.
MD5: A one-way hashing algorithm that produces a 128−bit hash.
SHA1: A one-way hashing algorithm that produces a 160−bit hash.
Encryption: Select the encryption method from the pull-down menu. There are four options, DES, 3DES, AES and
NULL. NULL means that it is a tunnel with no encryption. 3DES and AES are more powerful but increase latency.
DES: Stands for Data Encryption Standard, it uses 56 bits as an encryption method.
3DES: Stands for Triple Data Encryption Standard, it uses 168 (56*3) bits as an encryption method.
AES: Stands for Advanced Encryption Standards, it uses 128 bits as an encryption method.
Perfect Forward Secrecy: Choose whether to enable PFS using Diffie-Hellman public-key cryptography to change
encryption keys during the second phase of VPN negotiation. This function will provide better security, but extends the
VPN negotiation time. Diffie-Hellman is a public-key cryptography protocol that allows two parties to establish a shared
secret over an unsecured communication channel (i.e. over the Internet). There are three modes, MODP 768-bit, MODP
1024-bit and MODP 1536-bit. MODP stands for Modular Exponentiation Groups.
Pre-shared Key: This is for the Internet Key Exchange (IKE) protocol, a string from 4 to 128 characters. Both sides
should use the same key. IKE is used to establish a shared security policy and authenticated keys for services (such as
IPSec) that require a key. Before any IPSec traffic can be passed, each router must be able to verify the identity of its
peer. This can be done by manually entering the pre-shared key into both sides (router or hosts).