Virtual Private Networking Using IPSec and L2TP Connections
240
NETGEAR ProSAFE VPN Firewall FVS318G v2
Each policy contains the data that is described in the following table. These fields are
described in more detail in
Table 51
on page 243.
You cannot delete or edit an IKE policy for which the VPN policy is active without first
disabling or deleting the VPN policy.
To delete one or more IKE polices:
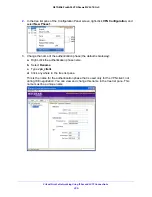
1.
Log in to the unit:
a.
In the address field of any of the qualified web browsers, enter
https://192.168.1.1
.
The NETGEAR Configuration Manager Login screen displays.
b.
In the
Username
field, enter
admin
and in the
Password / Passcode
field, enter
password
.
Use lowercase letters. If you changed the password, enter your personalized
password. Leave the domain as it is (geardomain).
c.
Click the
Login
button.
The Router Status screen displays. After five minutes of inactivity, which is the default
login time-out, you are automatically logged out.
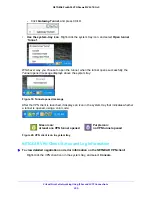
2.
Select
VPN > IPSec VPN
.
The IKE Policies screen displays.
3.
Select the check box to the left of each policy that you want to delete or click the
Select All
table button to select all IKE policies.
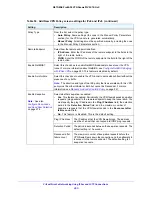
Table 50. IKE Policies screen information for IPv4 and IPv6
Item
Description
Name
The name that identifies the IKE policy. When you use the VPN Wizard to set up a
VPN policy, an accompanying IKE policy is automatically created with the same
name that you select for the VPN policy.
Note:
The name is not supplied to the remote VPN endpoint.
Mode
The exchange mode: Main or Aggressive.
Local ID
The IKE/ISAKMP identifier of the VPN firewall. The remote endpoint must use this
value as its remote ID.
Remote ID
The IKE/ISAKMP identifier of the remote endpoint, which must use the this value as
its local ID.
Encr
The encryption algorithm that is used for the IKE security association (SA). This
setting must match the setting on the remote endpoint.
Auth
The authentication algorithm that is used for the IKE SA. This setting must use
match setting on the remote endpoint.
DH
The Diffie-Hellman (DH) group that is used when keys are exchanged. This setting
must match the setting on the remote endpoint.