DGFV338 ProSafe Wireless ADSL Modem VPN Firewall Router Reference Manual
7-12
LAN Configuration
v1.0, May 2008
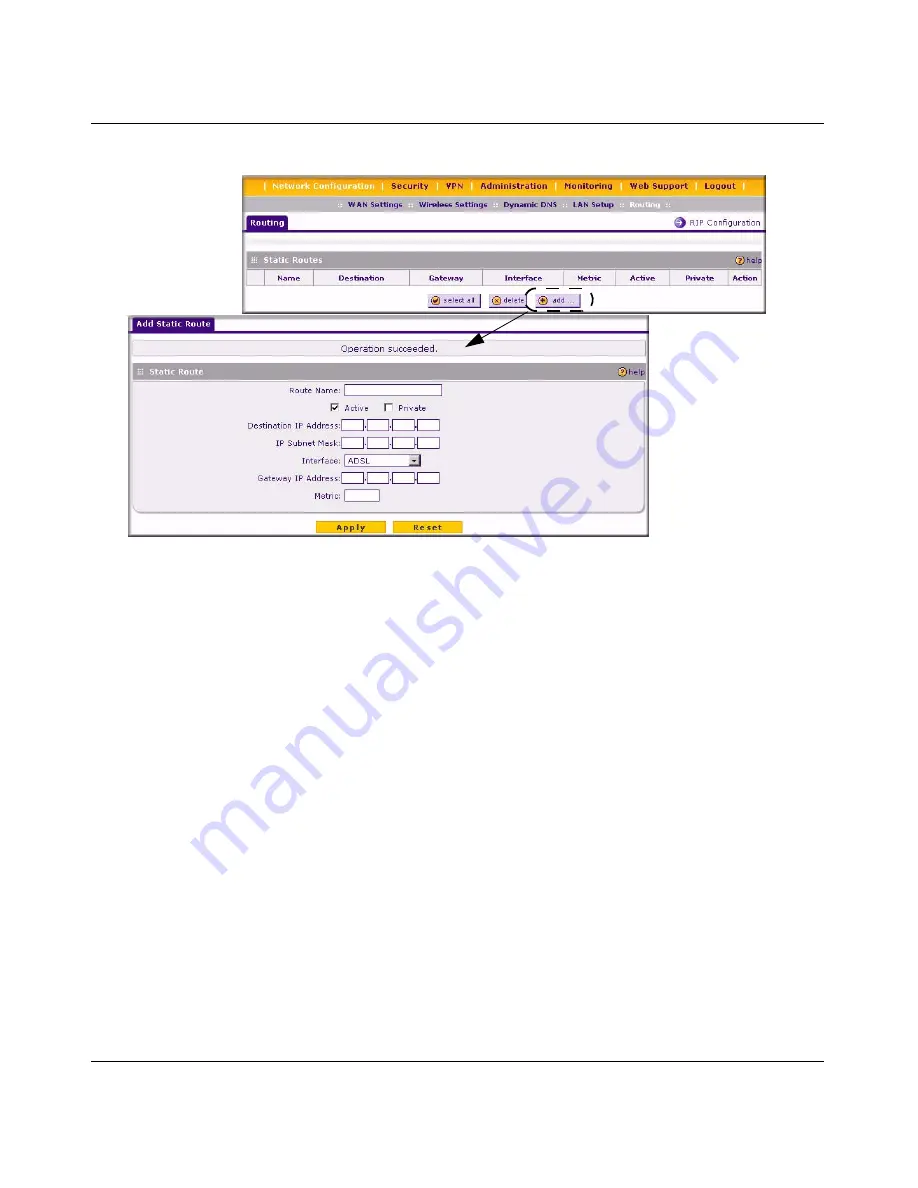
4.
Select
Active
to make this route effective.
5.
Select
Private
if you want to limit access to the LAN only. The private static route will not be
advertised in RIP.
6.
Enter the
Destination IP Address
to the host or network to which the route leads.
7.
Enter the
IP Subnet Mask
for this destination. If the destination is a single host, enter
255.255.255.255.
8.
Enter the
Interface
which is the physical network interface (ADSL, WAN Ethernet, or LAN)
through which the destination host or network is accessible.
9.
Enter the
Gateway IP Address
through which the destination host or network can be reached
(must be a router on the same LAN segment as the DGFV338).
10.
Enter the
Metric
priority for this route. If multiple routes to the same destination exit, the
route with the lowest metric is chosen (value must be between 1 and 15).
11.
Click
Apply
to save your settings. The new static route will be added to Static Routes table.
You can edit the settings of a static route in the Static Routes table by clicking
Edit
in the Action
column adjacent to the route.
Figure 7-7






























