Using the SecureCast Service to Get New Data Files
178
McAfee VirusScan Anti-Virus Software
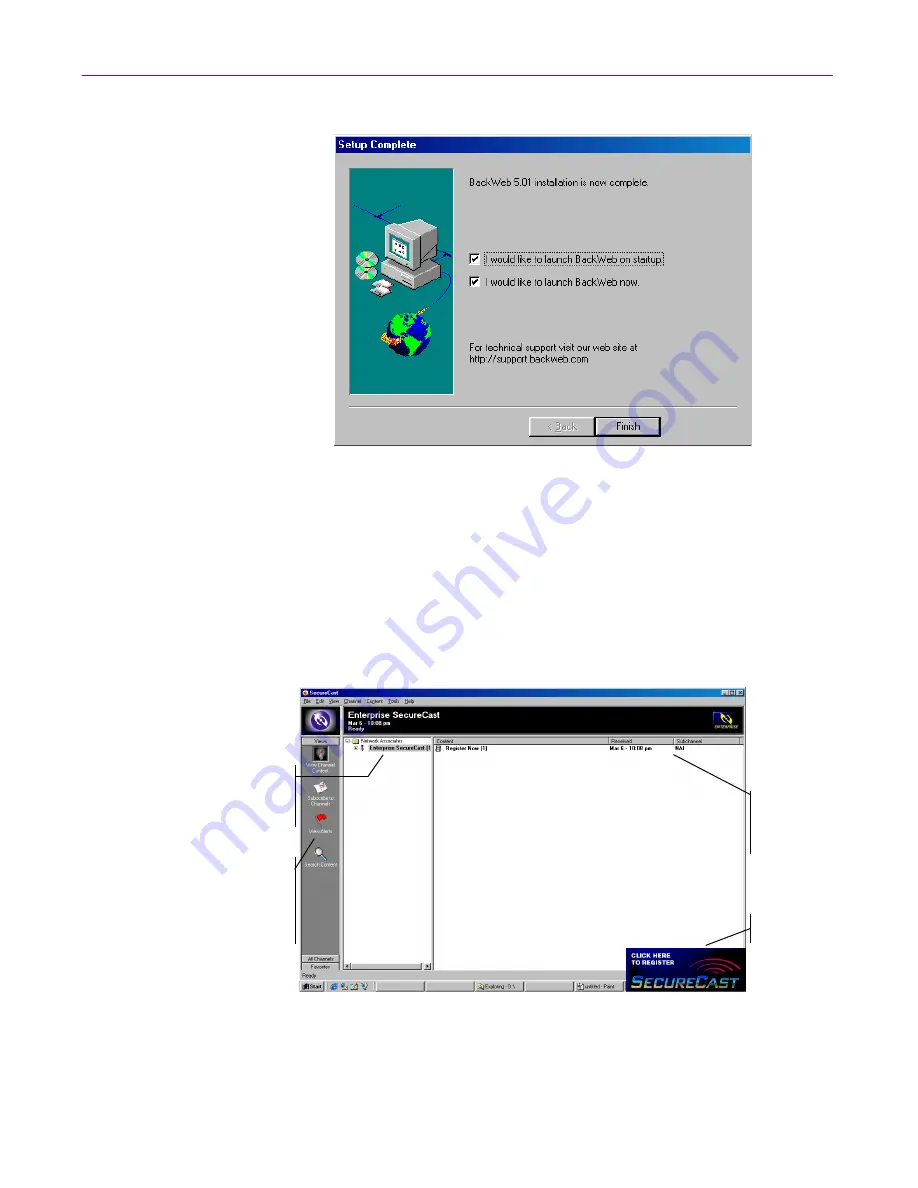
The Setup Complete
panel appears (
Figure D-8
).
Figure D-8. Setup Complete panel
13. To start immediately, leave both checkboxes selected in this panel, then
click
Finish
to complete your installation.
Phase 2: Register with the Enterprise SecureCast service
After you install the BackWeb client and start it, the SecureCast service
immediately opens the client application and sends its first InfoPak: the
SecureCast registration forms (
Figure D-9
).
Figure D-9. The Enterprise SecureCast client window
InfoPaks
downloaded
to your
system
appear here.
SecureCast
Flash Banner
SecureCast
channels to
which you
subscribe
appear here.
Choose
which
service
information
you want to
see in this
area.
Summary of Contents for VIRUSSCAN 4.5 -
Page 1: ...McAfee VirusScan Administrator s Guide Version 4 5...
Page 32: ...About VirusScan Software 32 McAfee VirusScan Anti Virus Software...
Page 96: ...Removing Infections From Your System 96 McAfee VirusScan Anti Virus Software...
Page 132: ...Updating and Upgrading VirusScan Software 132 McAfee VirusScan Anti Virus Software...
Page 170: ...Using VirusScan Command line Options 170 McAfee VirusScan Anti Virus Software...
















































