Lantronix
SM12XPA Web User Guide
33848 Rev. A
Page
333
of
473
Virtual Link
This page shows the OSPF virtual link configuration table. The virtual link is established between two ABRs to
overcome the fact that all the areas must be connected directly to the backbone area.
The backbone must be contiguous, but it does not need to be physically contiguous. Backbone connectivity
can be established and maintained by the configuration of “virtual links”.
Virtual links can be configured between any two backbone routers that have an interface to a common non-
backbone area. Virtual links belong to the backbone. The protocol treats two routers joined by a virtual link
as if they were connected by an unnumbered point-to-point backbone network. The routing protocol traffic
that flows along the virtual link uses intra-area routing only.
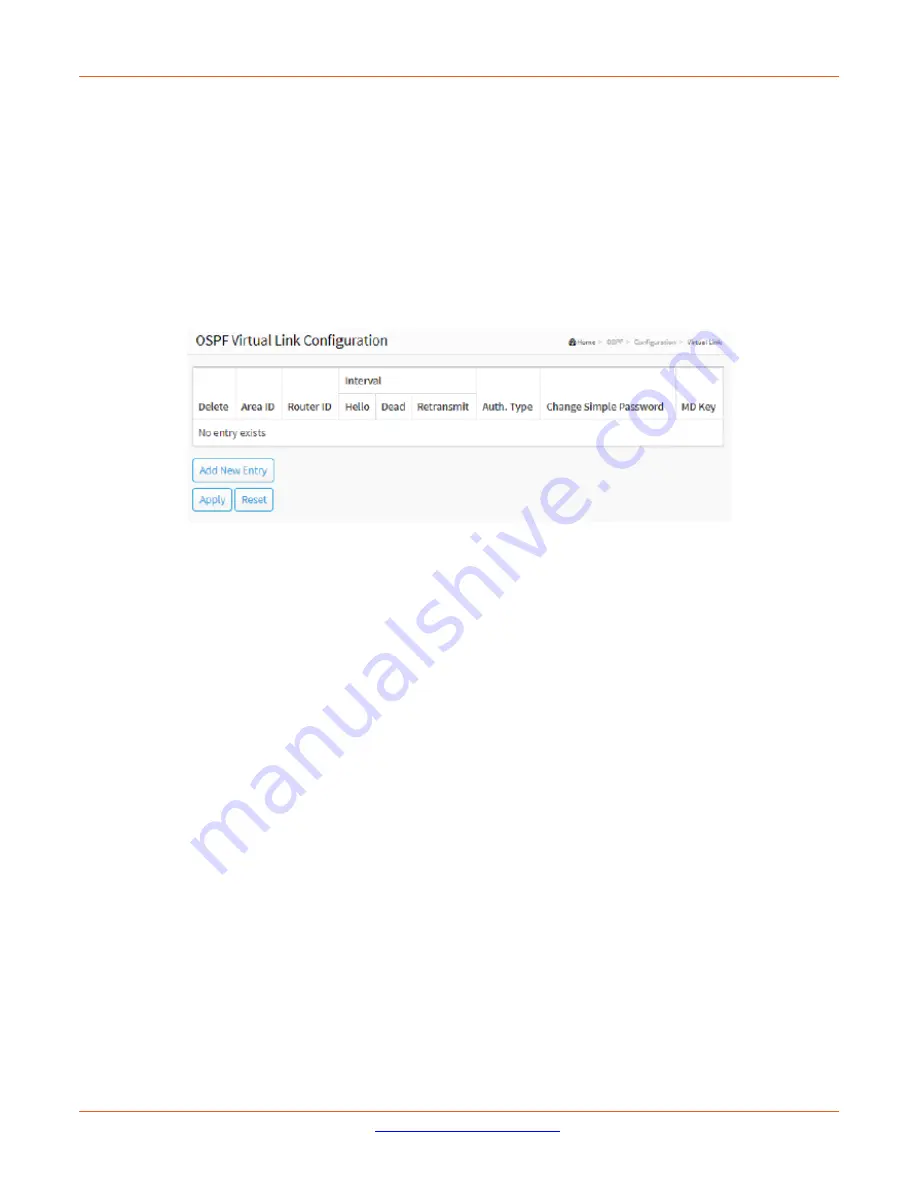
OSPF Virtual Link Configuration
Parameter descriptions
:
Delete
: Check to delete the entry. It will be deleted during the next save.
Area ID
: The OSPF Area ID.
Router ID
: The OSPF router ID.
Hello Interval
: The time interval (in seconds) between hello packets. The valid range is 1 to 65535 seconds and
the default value is 10 seconds.
OSPF uses Hello packets and two timers to check if a neighbor is still alive:
Hello
Interval
defines how often the hello packet is sent.
Dead
Interval
defines how long to wait for hello packets before declaring the neighbor dead.
The Hello and the Dead interval values can be different based on the OSPF network type.
Dead Interval
: The number of seconds to wait until the neighbor is declared to be dead. The valid range is
1 to 65535 seconds and the default value is 40 seconds.
Retransmit Interval
: The time interval (in seconds) between link-state advertisement (LSA) retransmissions for
adjacencies. The valid range is 3 to 65535 and the default value is 5 seconds.
Auth. Type
: The authentication type on an area.
Simple Password
: It's using a plain text authentication. A password must be configured, but the
password can be read by packet sniffers.
Message Digest
: It's message-digest algorithm 5 (MD5) authentication. Keying material must also be
configured. This is the most secure method.
Null Authentication
: No authentication.
Area Configuration
: Refer to
Area Authentication
setting on page
317
.