257
IPv6 static route configuration example
Network requirements
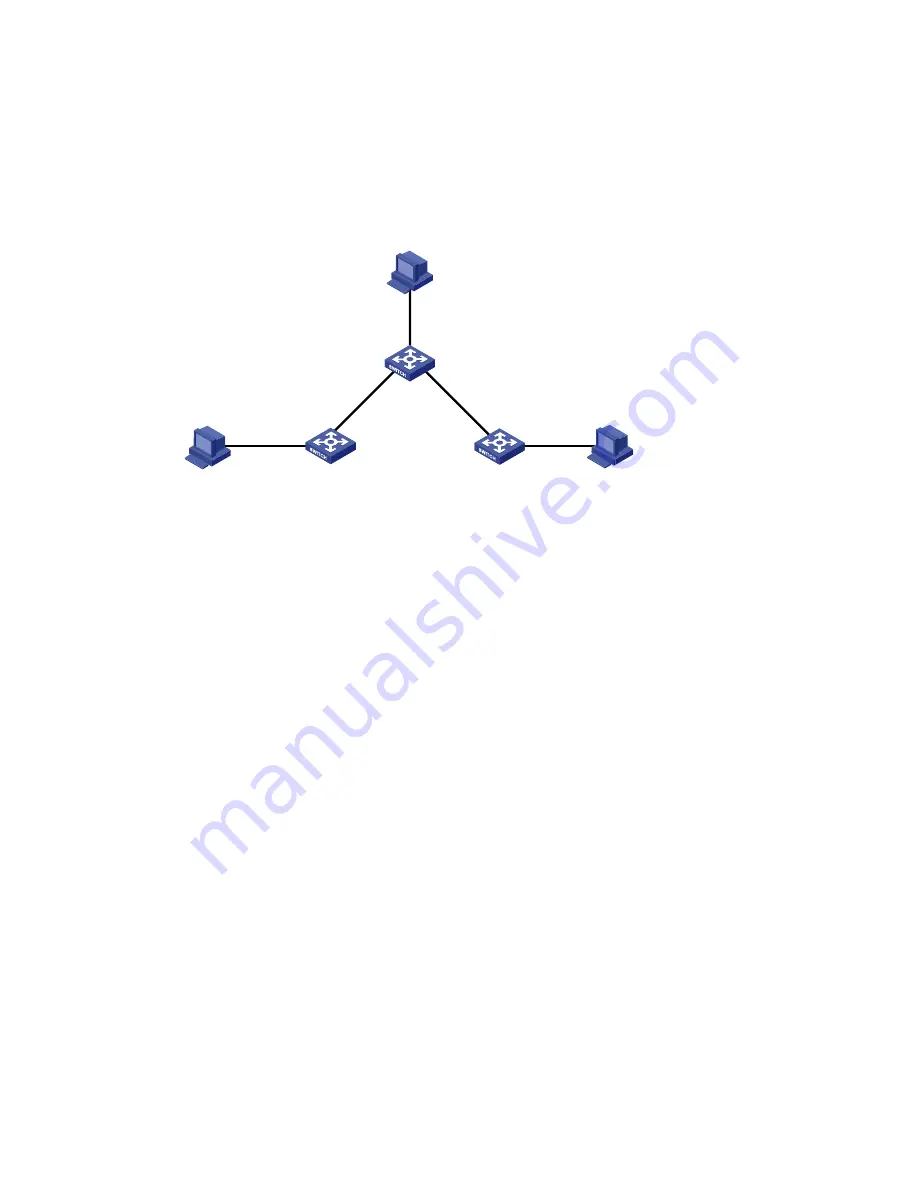
The IP addresses of devices are shown in
Figure 240
. IPv6 static routes need to be configured on Switch
A, Switch B and Switch C for any two hosts to communicate with each other.
Figure 240
Network diagram
Configuration considerations
1.
On Switch A, configure a default route with Switch B as the next hop.
2.
On Switch B, configure one static route with Switch A as the next hop and the other with Switch C
as the next hop.
3.
On Switch C, configure a default route with Switch B as the next hop.
Configuration procedure
1.
Configure a default route to Switch B on Switch A:
a.
Select
Network
>
IPv6 Routing
from the navigation tree of Switch A.
b.
Click the
Create
tab.
c.
Enter
::
for
Destination IP Address
, select
0
from the
Prefix Length
list, and enter
4::2
for
Next
Hop
.
d.
Click
Apply
.
Vlan-int400
2::1/64
Host B
2::2/64
Vlan-int200
4::2/64
Vlan-int300
5::2/64
Vlan-int200
4::1/64
Vlan-int300
5::1/64
Vlan-int500
3::1/64
Vlan-int100
1::1/64
Host A
1::2/64
Host C
3::2/64
Switch B
Switch A
Switch C
Summary of Contents for HP 830 Series
Page 37: ...25 Figure 18 Configuration complete ...
Page 70: ...58 Figure 49 Displaying the rate settings of ports ...
Page 78: ...66 Figure 56 Configuring the monitor port ...
Page 82: ...70 Figure 59 Switching to the management level ...
Page 87: ...75 Figure 64 Displaying port traffic statistics ...
Page 167: ...155 Figure 154 Displaying the current voice VLAN information ...
Page 304: ...292 Figure 280 Traceroute operation result ...
Page 321: ...309 Request timed out Ping statistics for 10 0 0 1 Packets Sent 4 Received 0 Lost 4 100 loss ...
Page 343: ...331 Figure 330 Ping operation summary ...






























