3-50
Configuration procedure
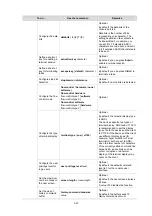
Follow these steps to configure the SSH client to log in to the SSH server:
To do…
Use the command…
Remarks
Log in to an IPv4 SSH server
ssh2
server
Required
server
is the IPv4 address or host
name of the server.
Available in user view
Log in to an IPv6 SSH server
ssh2
ipv6
server
Required
server
is the IPv6 address or host
name of the server.
Available in user view
You can configure other settings for the SSH client to work with the SSH server. For more information,
see
SSH2.0
in the
Security Command Reference
.
Logging In Through the AUX Port
Introduction
As shown in
, the console cable used in AUX port login is the same as that in console port
login. For a device that has separate console and AUX ports, you can use both to log in to the device to
facilitate system maintenance.
Figure 3-16
AUX port login diagram
By default, AUX port login adopts password authentication. To log in through the AUX port, log in to the
device through the console port or another method, configure the password for AUX password
authentication or change the authentication mode, and configure related parameters.
This section includes these topics:
z
AUX Login Authentication Modes
z
Configuring None Authentication for AUX Login
z
Configuring Password Authentication for AUX Login
z
Configuring Scheme Authentication for AUX Login
z
Configuring Common Settings for AUX Login (Optional)
z
z
Summary of Contents for SR6600 SPE-FWM
Page 112: ...6 101...