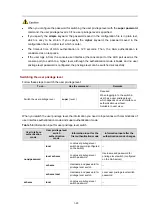
1-9
Hotkey
Function
Esc+N
Moves the cursor down by one line (available before you press
Enter
)
Esc+P
Moves the cursor up by one line (available before you press
Enter
)
Esc+<
Specifies the cursor as the beginning of the clipboard.
Esc+>
Specifies the cursor as the ending of the clipboard.
The hotkeys in the table above are defined by the switch. If the same hotkeys are defined by the
terminal software that you use to interact with the switch, the hotkeys defined by the terminal software
take effect.
Redisplaying Input But Not Submitted Commands
If your command input is interrupted by output system information, you can use this feature to redisplay
the previously input but not submitted commands so that you can continue your operation from where
you were stopped.
Follow these steps to enable redisplaying of input but not submitted commands:
To do…
Use the command…
Remarks
Enter system view
system-view
—
Enable redisplaying of input but
not submitted commands
info-center synchronous
Required
Disabled by default
With this feature enabled:
z
If you have no input at the command line prompt and the system outputs system information such
as logs, the system will not display the command line prompt after the output.
z
If the system outputs system information when you are typing interactive information (not YES/NO
for confirmation), the system will not redisplay the prompt information but a line break after the
output and then display what you have typed.
z
For more information about the
info-center synchronous
command, see
Information Center
in
the
Network Management and Monitoring Configuration Guide
.
Checking Command Line Errors
If a command contains syntax errors, the CLI reports error information.
lists some common
command line errors.
Summary of Contents for SR6600 SPE-FWM
Page 112: ...6 101...