TRENDnet User’s Guide
TV‐IP328PI
© Copyright TRENDnet. All Rights Reserved.
35
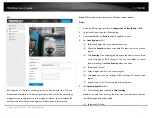
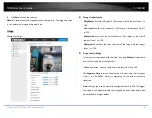
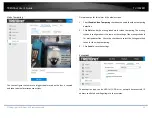
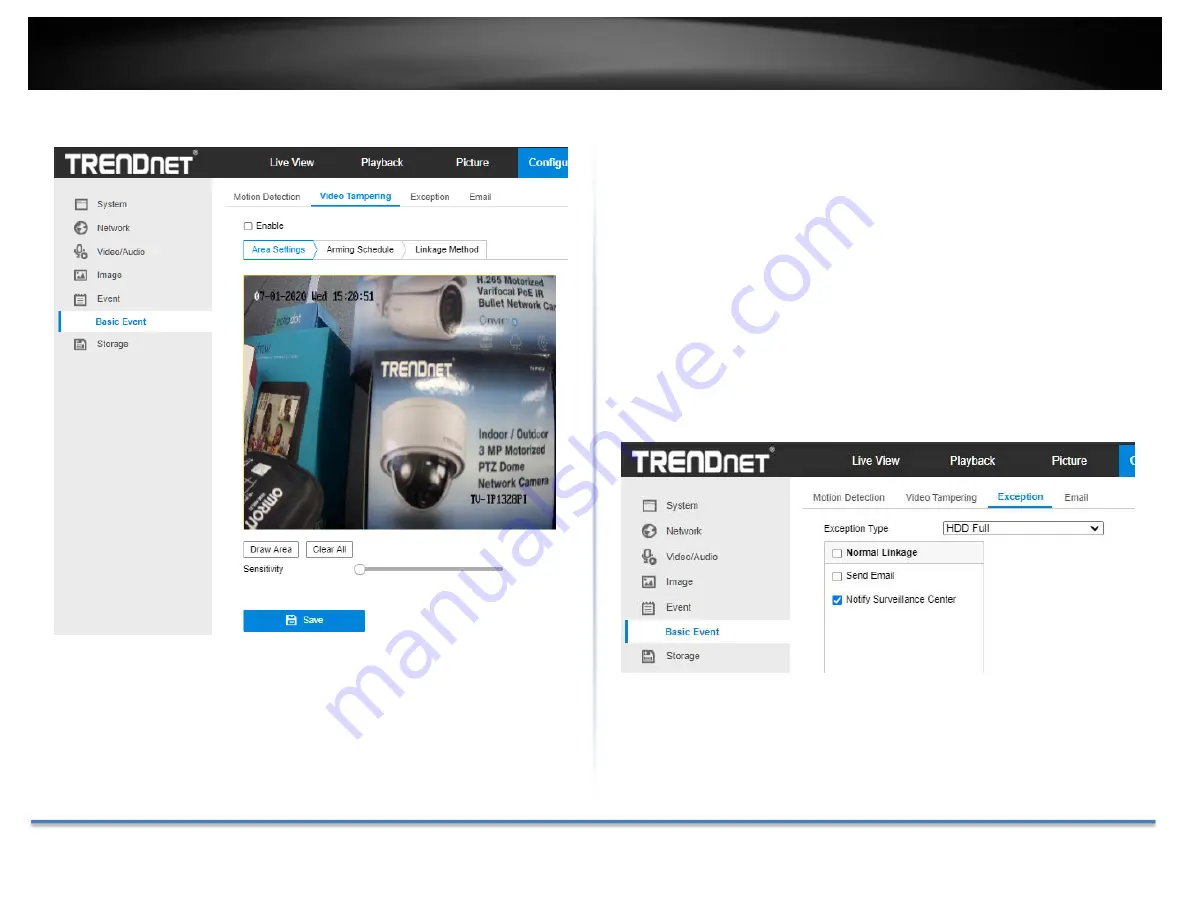
Video Tampering
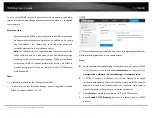
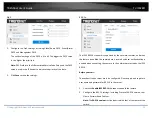
You can configure the camera to trigger the alarm when the lens is covered
and take certain alarm response actions.
Detection area for this alarm is the whole screen.
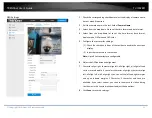
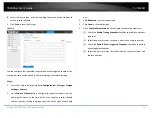
1.
Check
Enable Video Tampering
checkbox to enable the video tampering
detection.
2.
Click
Edit
to edit the arming schedule for video tampering. The arming
schedule configuration is the same as the setting of the arming schedule
for motion detection. Check the checkbox to select the linkage method
taken for the video tampering.
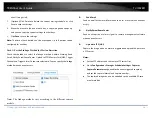
3.
Click
Save
to save the settings.
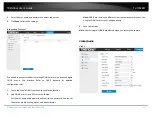
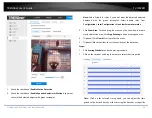
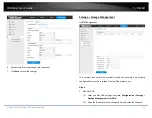
Exceptions
The exception type can be HDD full, HDD error, network disconnected, IP
address conflicted and illegal login to the cameras.