● DNS Server Address
Shows the IP address of the DNS server.
● Origin
Shows whether the DNS server was configured manually or was assigned by DHCP.
4.5.16.2
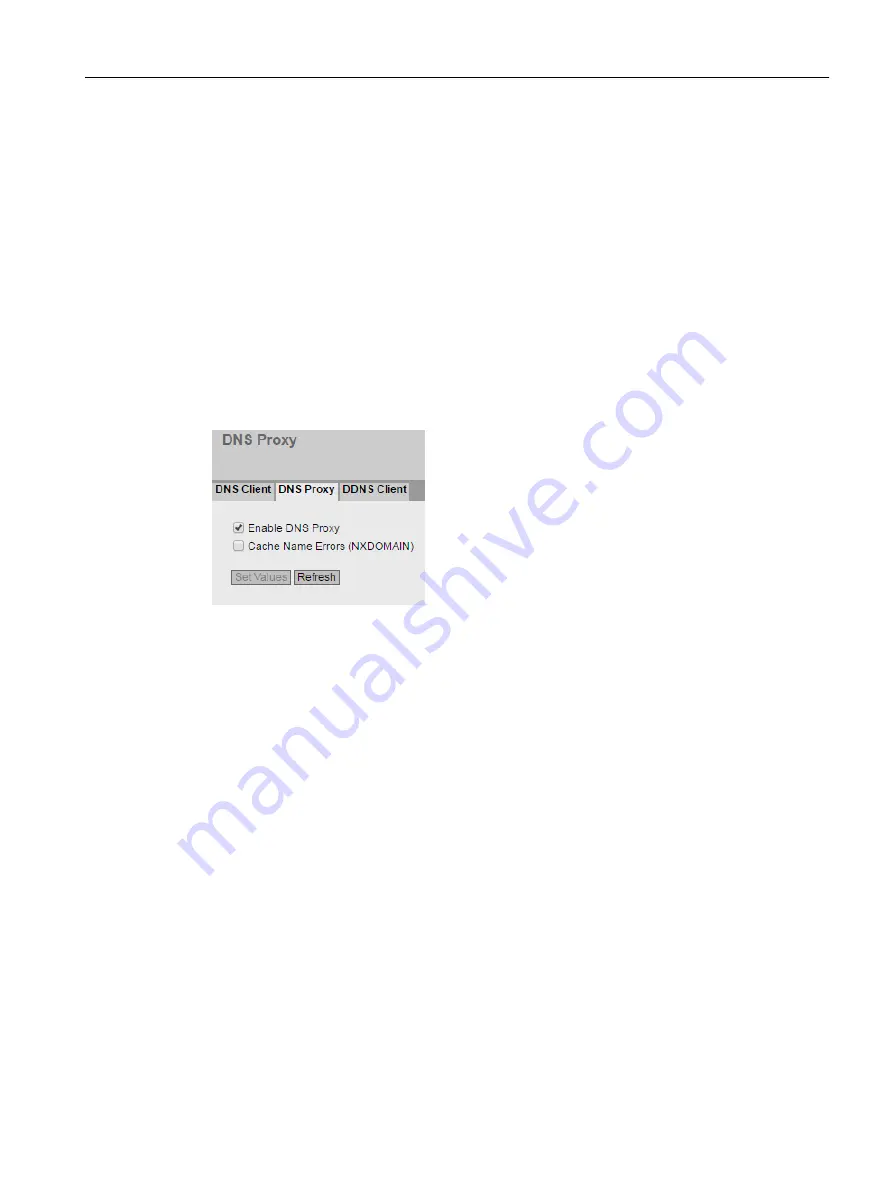
DNS Proxy
The device provides a DNS server for the local network. If you enter the IP address of the device
in the local application as a DNS server, then the device answers the DNS requests from its
cache.
If the device does not know the IP address for a domain address, it forwards the query to an
external DNS server. How long the device keeps a domain address in the cache depends on
the host being addressed. In addition to the IP address, a DNS request to an external DNS
server also supplies the life span of this information.
Description
The page contains the following boxes:
● Enable DNS Proxy
Enable or disable the proxy of the DNS server.
● Cache Name Errors (NXDOMAIN)
Enable or disable the caching of NXDOMAIN replies. If you enable the option, the domain
names that were unknown to the DNS server remain in the cache.
4.5.16.3
DDNS Client
The DDNS (Dynamic Domain Name System) is an Internet service that allows a fixed
hostname to be set up as a pseudonym for a dynamically changing IP address.
The DDNS client synchronizes the assigned IP address with the hostname registered at the
DDNS provider. This means that the device can always be reached using the same hostname.
Configuring with Web Based Management
4.5 "System" menu
SCALANCE S615 Web Based Management
Configuration Manual, 11/2019, C79000-G8976-C388-08
189
Содержание SIMATIC NET SCALANCE S615
Страница 12: ...Table of contents SCALANCE S615 Web Based Management 12 Configuration Manual 11 2019 C79000 G8976 C388 08 ...
Страница 24: ...Description 1 7 PLUG SCALANCE S615 Web Based Management 24 Configuration Manual 11 2019 C79000 G8976 C388 08 ...
Страница 316: ...Appendix A A 3 Syslog messages SCALANCE S615 Web Based Management 316 Configuration Manual 11 2019 C79000 G8976 C388 08 ...
Страница 320: ...Index SCALANCE S615 Web Based Management 320 Configuration Manual 11 2019 C79000 G8976 C388 08 ...






























