Nortel Switched Firewall 2.3.3 User’s Guide and Command Reference
Initial setup
81
213455-L, October 2005
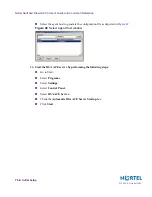
Enabling SecurID authentication for Check Point FireWall-1 users
To enable SecurID authentication for Check Point FireWall-1 users, perform the following
steps:
1.
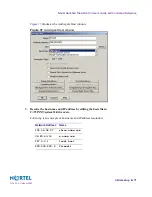
Create a new user group.
2.
Create a new user.
3.
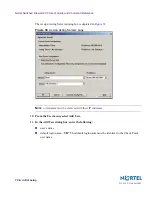
Add the new user to the new group.
4.
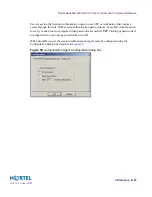
From the Authentication tab, select SecurID for the authentication scheme.
The newly created user is authenticated using the ACE server through the Firewalls by user
name and passcode from the token card.
Rule base for user authentication with SecurID
The following table is a rule base for user authentication with SecureID.
Rule 1 challenges users from any location trying to access any service.
Rule 2 is not required if the Firewall is configured to allow outgoing packets as part of the
Global Policy Properties.
Rule 3 drops all other packets.
N
OTE
–
The SecureID user name must exist on the web, FTP, or Telnet server.
Rule base for client authentication with SecurID
With client authentication, an administrator can grant access a specific source. For SecurID
users, client authentication permits authentication to the Firewall once, through HTTP or
Telnet, then opens any number of connections for any service, while the authentication is valid
for any Administrator-defined duration.
Rule
number
Source
Destination VPN
Service
Action
Track
1
kevlar@Any
* Any
Any Traffic Authenti-
cated
User Auth Log
2
ACE_Server
Cluster _HA
* Any
Any Traffic Securid
Accept
Log
3
* Any
* Any
Any Traffic * Any
Drop
None
Содержание 5100 Series Release 2.3.3
Страница 18: ...Nortel Switched Firewall 2 3 3 User s Guide and Command Reference 18 Preface 213455 L October 2005...
Страница 20: ...Nortel Switched Firewall 2 3 3 User s Guide and Command Reference 20 Getting started 213455 L October 2005...
Страница 28: ...Nortel Switched Firewall 2 3 3 User s Guide and Command Reference 28 Introduction 213455 L October 2005...
Страница 90: ...Nortel Switched Firewall 2 3 3 User s Guide and Command Reference 90 Initial setup 213455 L October 2005...
Страница 188: ...Nortel Switched Firewall 2 3 3 User s Guide and Command Reference 188 Redundant Firewalls 213455 L October 2005...
Страница 228: ...Nortel Switched Firewall 2 3 3 User s Guide and Command Reference 228 Applications 213455 L October 2005...
Страница 248: ...Nortel Switched Firewall 2 3 3 User s Guide and Command Reference 248 Basic system management 213455 L October 2005...
Страница 250: ...Nortel Switched Firewall 2 3 3 User s Guide and Command Reference 250 Command reference 213455 L October 2005...
Страница 264: ...Nortel Switched Firewall 2 3 3 User s Guide and Command Reference 264 The Command Line Interface 213455 L October 2005...
Страница 374: ...Nortel Switched Firewall 2 3 3 User s Guide and Command Reference 374 Command reference 213455 L October 2005...
Страница 376: ...Nortel Switched Firewall 2 3 3 User s Guide and Command Reference 376 Appendices 213455 L October 2005...
Страница 406: ...Nortel Switched Firewall 2 3 3 User s Guide and Command Reference 406 Common tasks 213455 L October 2005...