Nortel Switched Firewall 2.3.3 User’s Guide and Command Reference
200
Layer 2 and Layer 3 Firewalls
213455-L, October 2005
Check Point disables address spoofing on bridge ports unless they are manually added to the
configuration (eth2 and eth3 are bridge ports).
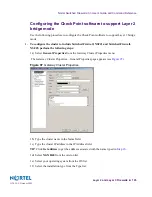
Figure 102
Gateway Cluster Properties NSF cluster—Topology
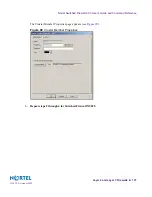
8.
Click Edit Topology.
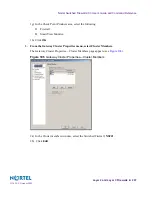
The Edit Topology page appears (see
Figure 103
).
Содержание 5100 Series Release 2.3.3
Страница 18: ...Nortel Switched Firewall 2 3 3 User s Guide and Command Reference 18 Preface 213455 L October 2005...
Страница 20: ...Nortel Switched Firewall 2 3 3 User s Guide and Command Reference 20 Getting started 213455 L October 2005...
Страница 28: ...Nortel Switched Firewall 2 3 3 User s Guide and Command Reference 28 Introduction 213455 L October 2005...
Страница 90: ...Nortel Switched Firewall 2 3 3 User s Guide and Command Reference 90 Initial setup 213455 L October 2005...
Страница 188: ...Nortel Switched Firewall 2 3 3 User s Guide and Command Reference 188 Redundant Firewalls 213455 L October 2005...
Страница 228: ...Nortel Switched Firewall 2 3 3 User s Guide and Command Reference 228 Applications 213455 L October 2005...
Страница 248: ...Nortel Switched Firewall 2 3 3 User s Guide and Command Reference 248 Basic system management 213455 L October 2005...
Страница 250: ...Nortel Switched Firewall 2 3 3 User s Guide and Command Reference 250 Command reference 213455 L October 2005...
Страница 264: ...Nortel Switched Firewall 2 3 3 User s Guide and Command Reference 264 The Command Line Interface 213455 L October 2005...
Страница 374: ...Nortel Switched Firewall 2 3 3 User s Guide and Command Reference 374 Command reference 213455 L October 2005...
Страница 376: ...Nortel Switched Firewall 2 3 3 User s Guide and Command Reference 376 Appendices 213455 L October 2005...
Страница 406: ...Nortel Switched Firewall 2 3 3 User s Guide and Command Reference 406 Common tasks 213455 L October 2005...