Dashboard 4 - 9
4.1.1.2.7 Wireless Clients
The
Wireless Clients
field displays information about the wireless clients managed by the selected access point.
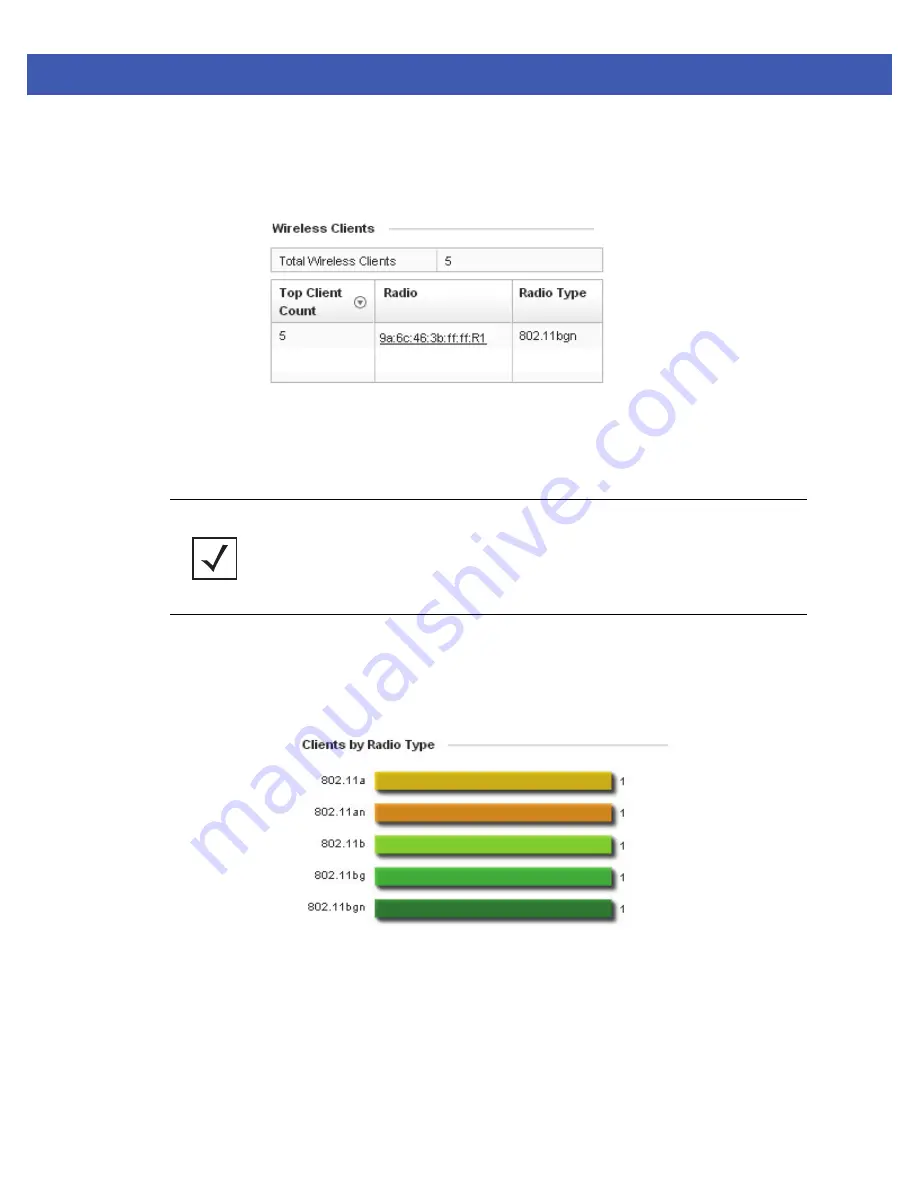
Figure 4-10
Wireless Clients field
Information within the
Wireless Clients
field is presented in two tables. The first table lists the total number of wireless
clients managed by this access point. The second table lists an ordered ranking of radios based on their supported client
count. Use this information to assess if an access point managed radio is optimally deployed in respect to its radio type
and intended client support requirements.
4.1.1.2.8 Clients by Radio Type
The
Clients by Radio Type
field displays a bar graph illustrating the number of connected clients currently operating on
supported radio bands.
Figure 4-11
Client On Channel field
For 5 GHz, clients are displayed supporting the
802.11a
and
802.11an
radio bands. For 2.4 GHz, clients are displayed
supporting the
802.11b
,
802.11bg
, and
802.11bgn
radio bands. Use this information to determine if all the access point’s
client radio bands are optimally supported for the access point’s radio coverage area.
NOTE:
AP-7131, AP-6532 and AP-7161 model access points can support up to 256 client
connections to a single access point. AP-6511 and AP-6521 model access points (both
single radio models) can support up to 128 client connections per access point.
Содержание WiNG 5
Страница 1: ...Motorola Solutions WiNG 5 Access Point System Reference Guide ...
Страница 2: ......
Страница 10: ...viii WiNG 5 Access Point System Reference Guide ...
Страница 16: ...1 4 WiNG 5 Access Point System Reference Guide ...
Страница 28: ...2 12 WiNG 5 Access Point System Reference Guide ...
Страница 48: ...3 20 WiNG 5 Access Point System Reference Guide ...
Страница 197: ...Device Configuration 5 137 Figure 5 78 Profile Management Settings screen ...
Страница 335: ...Device Configuration 5 275 Figure 5 155 Profile Overrides Management Settings screen ...
Страница 348: ...5 288 WiNG 5 Access Point System Reference Guide ...
Страница 350: ...6 2 WiNG 5 Access Point System Reference Guide Figure 6 1 Configuration Wireless ...
Страница 448: ...6 100 WiNG 5 Access Point System Reference Guide ...
Страница 492: ...8 32 WiNG 5 Access Point System Reference Guide ...
Страница 538: ...9 46 WiNG 5 Access Point System Reference Guide ...
Страница 564: ...11 10 WiNG 5 Access Point System Reference Guide ...
Страница 606: ...12 42 WiNG 5 Access Point System Reference Guide ...
Страница 732: ...13 126WiNG 5 Access Point System Reference Guide Figure 13 67 Access Point Certificate Trustpoint screen ...
Страница 762: ...A 2 WiNG 5 Access Point System Reference Guide ...
Страница 801: ......






























