330
| Intrusion Detection
Aruba Instant 6.5.0.0-4.3.0.0 | User Guide
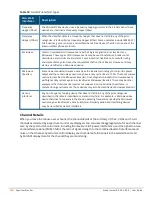
Detection Level
Detection Policy
l
Detect IAP Flood Attack
l
Detect Client Flood Attack
l
Detect Bad WEP
l
Detect CTS Rate Anomaly
l
Detect RTS Rate Anomaly
l
Detect Invalid Address Combination
l
Detect Malformed Frame—HT IE
l
Detect Malformed Frame—Association Request
l
Detect Malformed Frame—Auth
l
Detect Overflow IE
l
Detect Overflow EAPOL Key
l
Detect Beacon Wrong Channel
l
Detect devices with invalid MAC OUI
Table 67:
Infrastructure Detection Policies
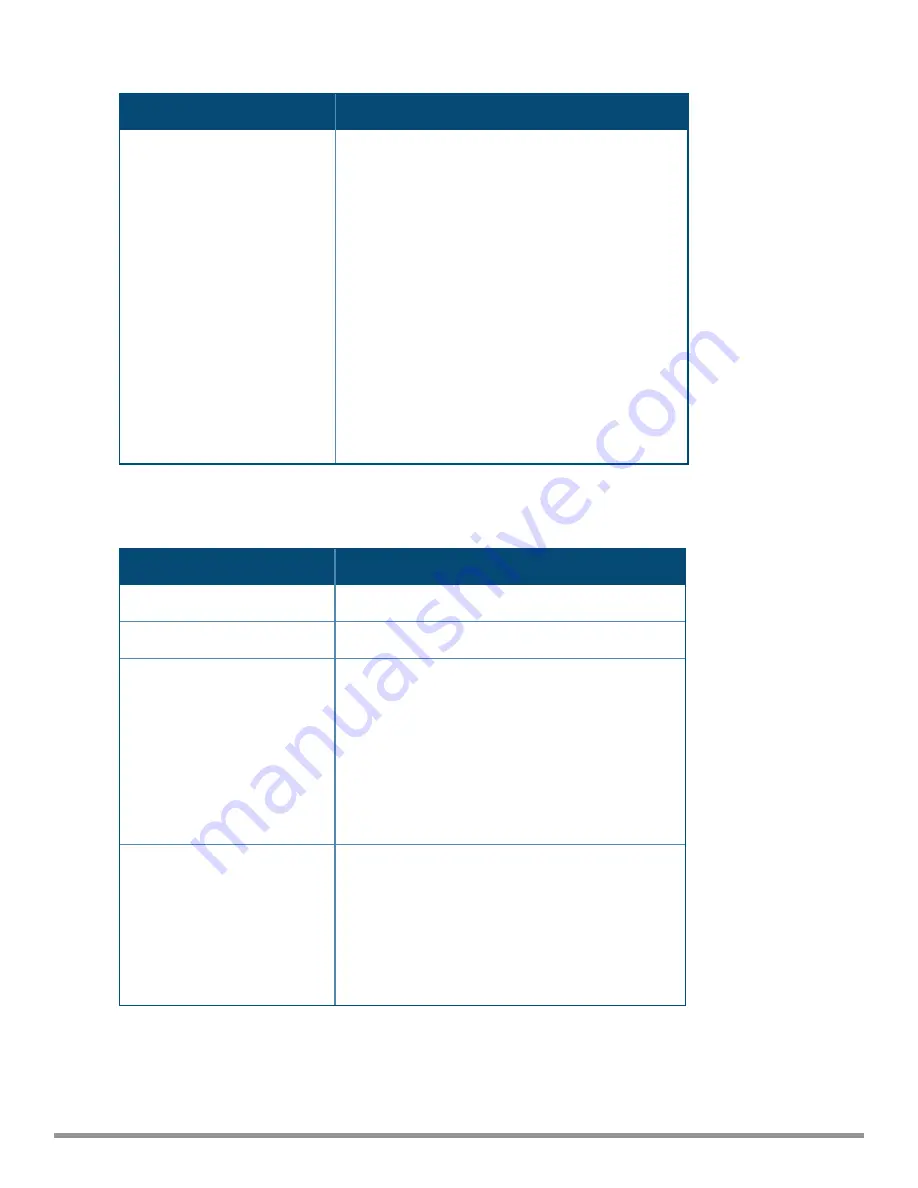
The following table describes the detection policies enabled in the Client Detection
Custom settings
text box.
Detection Level
Detection Policy
Off
All detection policies are disabled.
Low
l
Detect Valid Station Misassociation
Medium
l
Detect Disconnect Station Attack
l
Detect Omerta Attack
l
Detect FATA-Jack Attack
l
Detect Block ACK DOS
l
Detect Hotspotter Attack
l
Detect unencrypted Valid Client
l
Detect Power Save DOS Attack
High
l
Detect EAP Rate Anomaly
l
Detect Rate Anomaly
l
Detect Chop Chop Attack
l
Detect TKIP Replay Attack
l
IDS Signature—Air Jack
l
IDS Signature—ASLEAP
Table 68:
Client Detection Policies
The following levels of detection can be configured in the WIP Protection page:
l
Off
l
Low
l
High