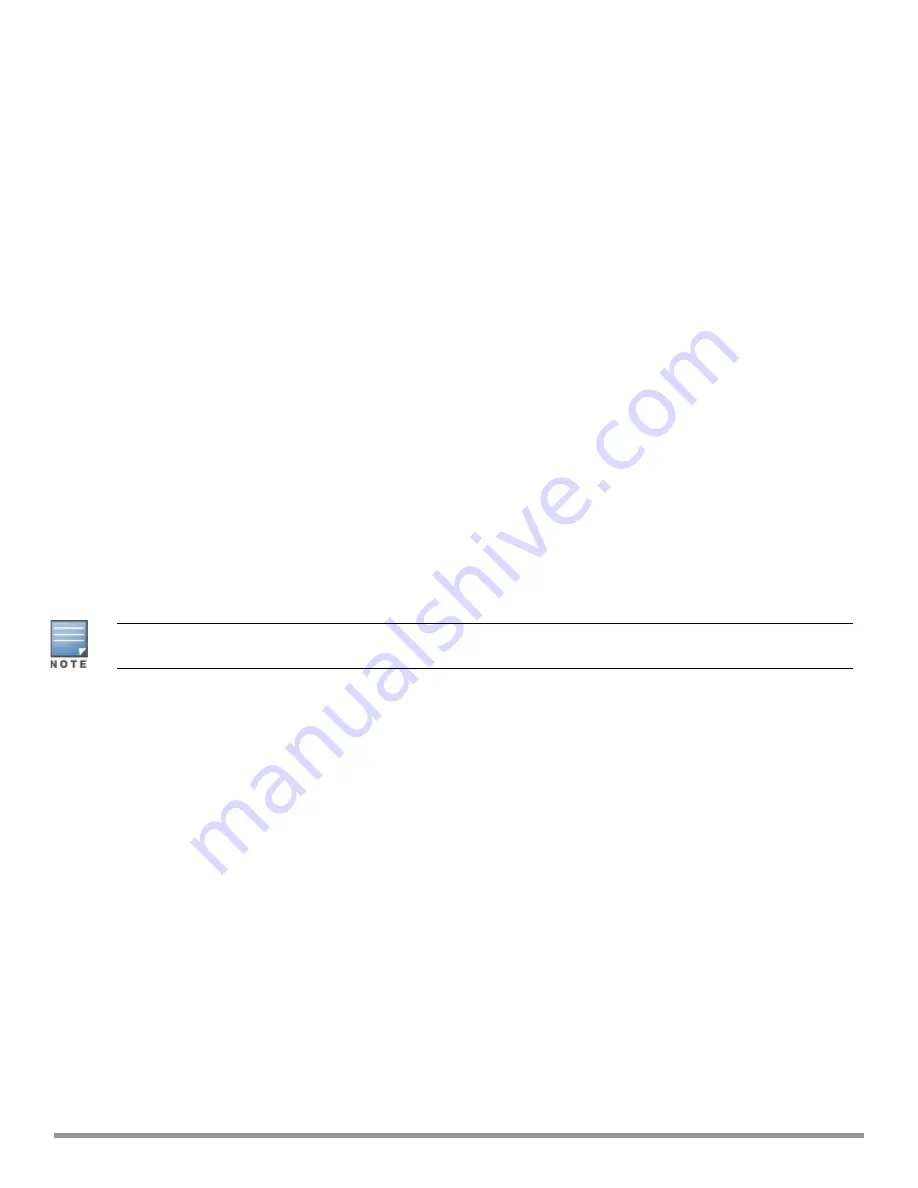
To view the attack statistics
(Instant AP)# show attack stats
attack counters
--------------------------------------
Counter
Value
-------
-------
arp packet counter
0
drop bad arp packet counter
0
dhcp response packet counter
0
fixed bad dhcp packet counter
0
send arp attack alert counter
0
send dhcp attack alert counter
0
arp poison check counter
0
garp send check counter
0
Configuring Firewall Settings to Disable Auto Topology Rules
By default, the auto topology rules in an IAP are enabled. You can disable the rules by configuring firewall
settings in the IAP.
In order to deny auto topology communication outside the IAP subnet, the inbound firewall settings must be
enabled.
When the inbound firewall settings are enabled:
l
Access Control Entities (ACEs) must be configured to block auto topology messages, as there is no default
rule at the top of predefined ACLs.
l
ACEs must be configured to override the guest VLAN auto-expanded ACEs. In other words, the user defined
ACEs take higher precedence over guest VLAN ACEs.
For more information on inbound firewall settings, see
The priority of a particular ACE is determined based on the order in which it is programmed. Ensure that you
do not accidentally override the guest VLAN ACEs.
You can change the status of auto topology rules by using the Instant UI or the CLI:
In the Instant UI
1. Click the
Security
located directly above the Search bar in the Instant main window.
2. Go to the
Firewall Settings
tab.
3. In
Firewall
section, select
Disabled
from the
Auto topology rules
drop-down list.
4. Click
OK
.
In the CLI
(Instant AP)(config)# firewall
(Instant AP)(firewall)# disable-auto-topology-rules
(Instant AP)(firewall)# end
(Instant AP)# commit apply
To view the configuration status:
Firewall
--------
Type
Value
----
-----
Auto topology rules
disable
Aruba Instant 6.5.0.0-4.3.0.0 | User Guide
Roles and Policies |
190






























