247
| IAP-VPN Deployment
Aruba Instant 6.5.0.0-4.3.0.0 | User Guide
l
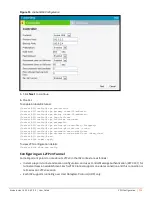
Centralized, L3
For more information on configuring DHCP profiles, see
Configuring DHCP Scopes on page 211
.
A Centralized, L2 or Distributed, L2 VLAN or subnet cannot be used to serve IAPs in a hierarchical mode of
deployment. Ensure that the physical IP of the IAPs connecting to the master IAP in hierarchical mode of
deployment is not on a VLAN or subnet that is in Centralized, L2 or Distributed, L2 mode of operation. For
information on hierarchical mode of deployment, see
Understanding Hierarchical Deployment on page 115
.
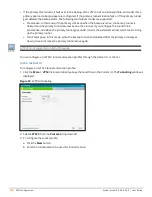
Configuring an SSID or Wired Port
For a client to connect to the IAP-VPN network, an SSID or wired port profile on an IAP must be configured with
appropriate IAP-VPN mode of operation. The VLAN configuration in an SSID or wired port profile determines
whether an SSID or wired port is configured for the IAP-VPN operations.
To configure an SSID or wired port for a specific IAP-VPN mode, the VLAN ID defined in the SSID or wired port
profile must match the VLAN ID defined in the DHCP profile configuration. If the VLAN assignment for an SSID
or wired port profile is set to VC assigned, custom, or a static VLAN ID that does not match the VLAN ID
configured in the DHCP profiles, the IAP-VPN operations are affected. For example, if a local DHCP profile is
configured with a VLAN ID of 200, the VLAN configuration on the SSID must be set to a static VLAN ID 200.
Ensure that the VLAN assignment for an SSID or wired port profile is not set to default as the VPN tunnel is
not supported on the default VLAN.
For information on how to configure an SSID or wired port profile, see
Wireless Network Profiles on page 81
and
Configuring a Wired Profile on page 108
, respectively.
Enabling Dynamic RADIUS Proxy
The RADIUS server can be deployed at different locations and VLANs. In most cases, a centralized RADIUS or
local server is used to authenticate users. However, some user networks can use a local RADIUS server for
employee authentication and a centralized RADIUS-based captive portal server for guest authentication. To
ensure that the RADIUS traffic is routed to the required RADIUS server, the dynamic RADIUS proxy feature
must be enabled. When enabled, dynamic RADIUS proxy ensures that all the RADIUS traffic is sourced from
the VC IP or inner IP of the IAP IPsec tunnel depending on the RADIUS server IP and routing profile.
Ensure that a static VC IP is configured before enabling dynamic RADIUS proxy in order to tunnel the RADIUS
traffic to the central RADIUS server in the datacenter.
For information on enabling dynamic RADIUS proxy, see
Configuring Dynamic RADIUS Proxy Parameters on
.
Configuring Enterprise Domains
By default, all the DNS requests from a client are forwarded to the client's DNS server. In a typical IAP
deployment without VPN configuration, client DNS requests are resolved by the DNS server of clients. For the
IAP-VPN scenario, the enterprise domain settings on the IAP are used to determine how client DNS requests
are routed. For information on how to configure enterprise domains, see
Configuring Enterprise Domains on
.
Configuring a Controller for IAP-VPN Operations
Aruba controllers provide an ability to terminate the IPsec and GRE VPN tunnels from the IAP and provide
corporate connectivity to the branch network.