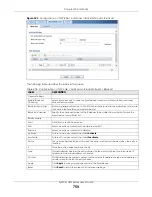
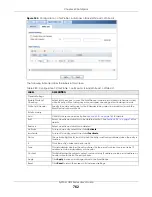
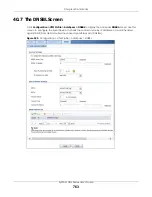
Chapter 39 Anti-Virus
ZyWALL USG Series User’s Guide
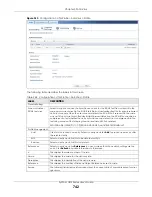
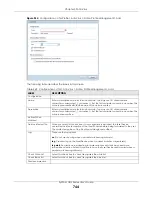
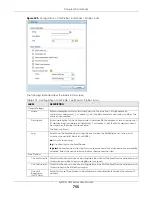
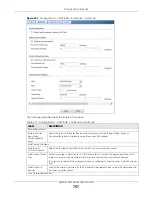
750
Computer Virus Infection and Prevention
The following describes a simple life cycle of a computer virus.
1
A computer gets a copy of a virus from a source such as the Internet, e-mail, file sharing or any
removable storage media. The virus is harmless until the execution of an infected program.
2
The virus spreads to other files and programs on the computer.
3
The infected files are unintentionally sent to another computer thus starting the spread of the virus.
4
Once the virus is spread through the network, the number of infected networked computers can grow
exponentially.
Types of Anti-Virus Scanner
The section describes two types of anti-virus scanner: host-based and network-based.
A host-based anti-virus (HAV) scanner is often software installed on computers and/or servers in the
network. It inspects files for virus patterns as they are moved in and out of the hard drive. However, host-
based anti-virus scanners cannot eliminate all viruses for a number of reasons:
• HAV scanners are slow in stopping virus threats through real-time traffic (such as from the Internet).
• HAV scanners may reduce computing performance as they also share the resources (such as CPU
time) on the computer for file inspection.
• You have to update the virus signatures and/or perform virus scans on all computers in the network
regularly.
A network-based anti-virus (NAV) scanner is often deployed as a dedicated security device (such as
your Zyxel Device) on the network edge. NAV scanners inspect real-time data traffic (such as E-mail
messages or web) that tends to bypass HAV scanners. The following lists some of the benefits of NAV
scanners.
• NAV scanners stop virus threats at the network edge before they enter or exit a network.
• NAV scanners reduce computing loading on computers as the read-time data traffic inspection is
done on a dedicated security device.
Summary of Contents for USG110
Page 27: ...27 PART I User s Guide ...
Page 195: ...195 PART II Technical Reference ...
Page 309: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 309 ...
Page 313: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 313 ...
Page 358: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 358 ...
Page 373: ...Chapter 10 Interfaces ZyWALL USG Series User s Guide 373 ...