xStack DGS-3400 Series Layer 2 Gigabit Ethernet Managed Switch
Multiple Image Services
The
Multiple Image Services
folder allows users of the Switch to configure and view information regarding firmware located on
the Switch. The Switch allows two firmware images to be stored in its memory and either can be configured to be the boot up
firmware for the Switch. For information regarding firmware images located on the Switch, open the
Firmware Information
link.
The default setting for the Switch’s firmware will have the boot up firmware stored in Image 1, but the user may set either
firmware stored to be the boot up firmware by using the
Config Firmware Image
menu.
Firmware Information
The following screen allows the user to view
information about current firmware images
stored on the Switch. To access the following
screen, click
Administration
> Multiple
Image Services > Firmware Information
.
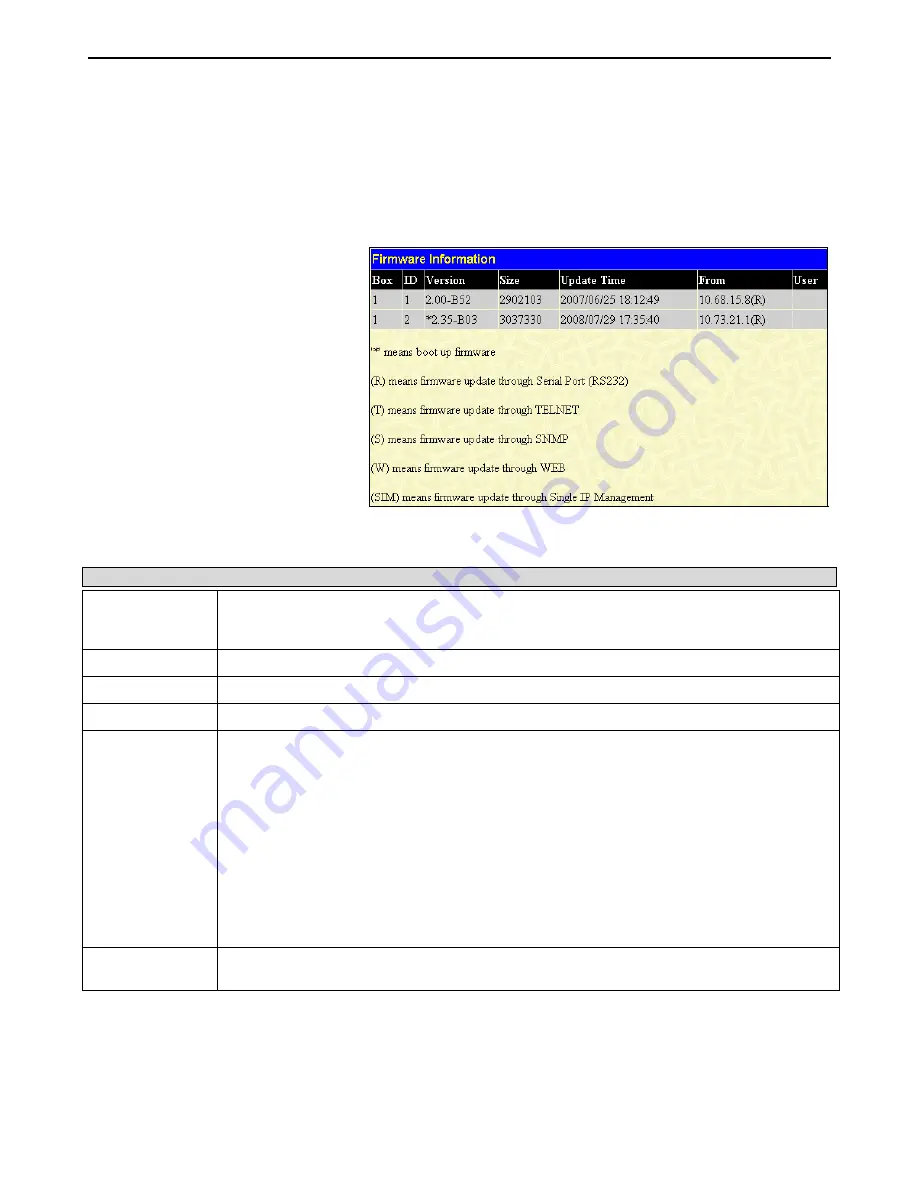
Figure 6- 30. Firmware Information window
This window holds the following information:
Parameter Description
ID
States the image ID number of the firmware in the Switch’s memory. The Switch can store 2
firmware images for use. Image ID 1 will be the default boot up firmware for the Switch unless
otherwise configured by the user.
Version
States the firmware version.
Size
States the size of the corresponding firmware, in bytes.
Update Time
States the specific time the firmware version was downloaded to the Switch.
From
States the IP address of the origin of the firmware. There are five ways firmware may be
downloaded to the Switch. Boot Up files are denoted by an asterisk (*) next to the file.
R – If the IP address has this letter attached to it, it denotes a firmware upgrade through the
Console Serial Port (RS-232).
T - If the IP address has this letter attached to it, it denotes a firmware upgrade through Telnet.
S - If the IP address has this letter attached to it, it denotes a firmware upgrade through the
Simple Network Management Protocol (SNMP).
W - If the IP address has this letter attached to it, it denotes a firmware upgrade through the web-
based management interface.
SIM – If the IP address has this letter attached to it, it denotes a firmware upgrade through the
Single IP Management feature.
User
States the user who downloaded the firmware. This field may read “Anonymous” or “Unknown”
for users that are not identified.
66
Summary of Contents for xStack DGS-3426
Page 321: ...307 BSMI Warning MIC Warning CCC Warning A...
Page 348: ...D Link D Link D Link D Link 495 744 00 99 http www dlink ru e mail support dlink ru...
Page 354: ...International Offices...
Page 356: ......






























