Hardware Installation
4-2
4
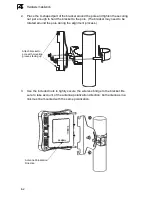
2.
Place the U-shaped part of the bracket around the pole and tighten the securing
nut just enough to hold the bracket to the pole. (The bracket may need to be
rotated around the pole during the alignment process.)
3.
Use the included nuts to tightly secure the wireless bridge to the bracket. Be
sure to take account of the antenna polarization direction; both antennas in a
link must be mounted with the same polarization.
Attach bracket to
pole with mounting
grooves facing up
Antenna Polarization
Direction
Summary of Contents for AWAP05O
Page 1: ...Dual Band Outdoor Access Point Bridge User Guide ...
Page 2: ......
Page 4: ...AWAP05O ZZ AWAP05OM ZZ F1 1 0 0 E072004 R01 150xxxxxxxxA ...
Page 28: ...Network Configuration 2 6 2 ...
Page 50: ...Initial Configuration 5 8 5 6 Click the OK button to restart the access point ...
Page 200: ...Troubleshooting A 2 A 5 If you forgot or lost the password Contact Technical Support ...
Page 212: ...Specifications B 12 B ...
Page 220: ...Glossary Glossary 4 ...
Page 224: ...Index 4 Index ...
Page 225: ......
Page 226: ...E032004 R01 150xxxxxxxxxA ...