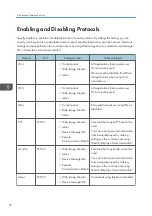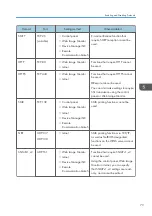
Enter the device certificate contents issued by the certificate authority.
1.
Log in as the network administrator from Web Image Monitor.
2.
Point to [Device Management], and then click [Configuration].
3.
Click [Device Certificate] under "Security".
4.
Check the radio button next to the number of the certificate you want to install.
To use SSL/TLS, select [Certificate 1]. To use any other protocol, select the certificate number you
want to use.
5.
Click [Install].
6.
Enter the contents of the device certificate.
In the certificate box, enter the contents of the device certificate issued by the certificate authority.
If you are installing an intermediate certificate, enter the contents of the intermediate certificate also.
For details about the displayed items and selectable items, see Web Image Monitor Help.
7.
Click [OK].
8.
Wait for about one or two minutes, and then click [OK].
"Installed" appears under "Certificate Status" to show that a device certificate for the machine has
been installed.
9.
Log out.
Installing an Intermediate Certificate (Issued by a Certificate Authority)
This section explains how to use Web Image Monitor to install an intermediate certificate issued by a
certificate authority.
If you do not have the intermediate certificate issued by the certificate authority, a warning message will
appear during communication. If the certificate authority has issued an intermediate certificate, we
recommend installing the intermediate certificate.
1.
Log in as the network administrator from Web Image Monitor.
2.
Point to [Device Management], and then click [Configuration].
3.
Click [Device Certificate] under "Security".
4.
Check the radio button next to the number of the certificate you want to install.
5.
Click [Install Intermediate Certificate].
6.
Enter the contents of the intermediate certificate.
In the certificate box, enter the contents of the intermediate certificate issued by the certificate
authority. For details about the items and settings of a certificate, see Web Image Monitor Help.
7.
Click [OK].
5. Enhanced Network Security
84
Содержание PRO C9100
Страница 2: ......
Страница 8: ...List of Operation Privileges for Address Books 229 INDEX 231 6...
Страница 24: ...1 Getting Started 22...
Страница 72: ...4 Preventing Leakage of Information from Machines 70...
Страница 116: ...5 Enhanced Network Security 114...
Страница 176: ...6 Managing the Machine 174...
Страница 188: ...7 Troubleshooting 186...
Страница 218: ...System Log Settings User Mach N W File Unset Set System Log R R R R R 8 List of Operation Privileges for Settings 216...
Страница 220: ...Settings User Mach N W File Unset Set Device Access Violation R W 8 List of Operation Privileges for Settings 218...
Страница 235: ......
Страница 236: ...EN GB EN US EN AU M238 1022 2014...