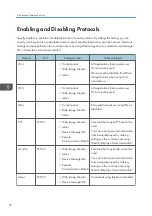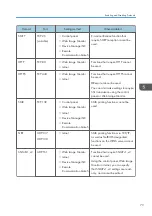
Protecting Communication Paths via a Device
Certificate
This machine can protect its communication paths and establish encrypted communications using SSL/
TLS, IPsec, or IEEE 802.1X.
To use these functions, it is necessary to create and install a device certificate for the machine in
advance.
The following types of device certificate can be used:
• Self-signed certificate created by the machine
• Certificate issued by a certificate authority
• The administrator is required to manage the expiration of certificates and renew the certificates
before they expire.
• The administrator is required to check that the issuer of the certificate is valid.
Creating and Installing a Device Certificate from the Control Panel (Self-Signed
Certificate)
Create and install the device certificate using control panel.
This section explains the use of a self-signed certificate as the device certificate.
1.
Log in as the network administrator from the control panel.
2.
Press [System Settings].
3.
Press [Administrator Tools].
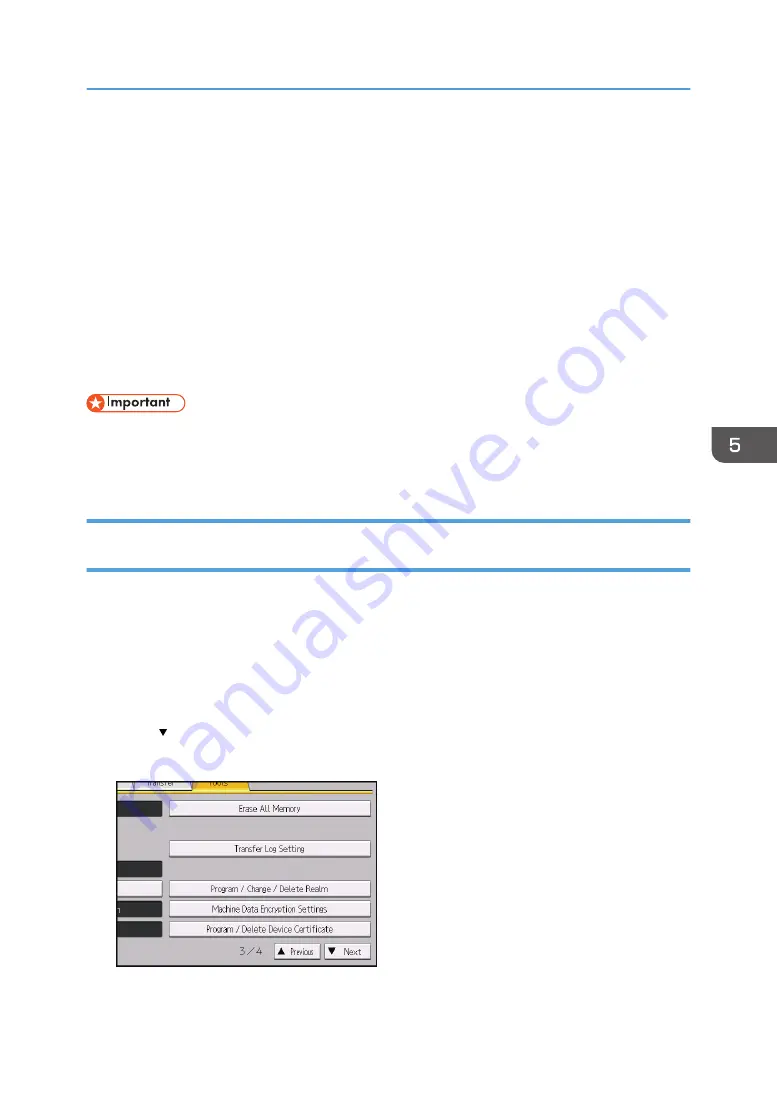
4.
Press [ Next] twice.
5.
Press [Program / Delete Device Certificate].
6.
Check that [Program] is selected.
Protecting Communication Paths via a Device Certificate
81
Содержание PRO C9100
Страница 2: ......
Страница 8: ...List of Operation Privileges for Address Books 229 INDEX 231 6...
Страница 24: ...1 Getting Started 22...
Страница 72: ...4 Preventing Leakage of Information from Machines 70...
Страница 116: ...5 Enhanced Network Security 114...
Страница 176: ...6 Managing the Machine 174...
Страница 188: ...7 Troubleshooting 186...
Страница 218: ...System Log Settings User Mach N W File Unset Set System Log R R R R R 8 List of Operation Privileges for Settings 216...
Страница 220: ...Settings User Mach N W File Unset Set Device Access Violation R W 8 List of Operation Privileges for Settings 218...
Страница 235: ......
Страница 236: ...EN GB EN US EN AU M238 1022 2014...