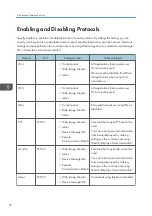
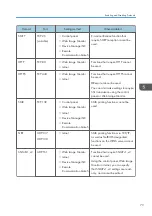
Creating a Device Certificate (Issued by a Certificate Authority)
Create the device certificate using Web Image Monitor. For details about the displayed items and
selectable items, see Web Image Monitor Help.
This section explains the use of a certificate issued by a certificate authority as the device certificate.
1.
Log in as the network administrator from Web Image Monitor.
2.
Point to [Device Management], and then click [Configuration].
3.
Click [Device Certificate] under "Security".
4.
Check the radio button next to the number of the certificate you want to create.
To use SSL/TLS, select [Certificate 1]. To use any other protocol, select the certificate number you
want to use.
5.
Click [Request].
6.
Configure the necessary settings.
7.
Click [OK].
The setting is changed.
8.
Click [OK].
"Requesting" appears for "Certificate Status".
9.
Log out.
10.
Apply to the certificate authority for the device certificate.
The application procedure depends on the certificate authority. For details, contact the certificate
authority.
For the application, click Web Image Monitor Details icon and use the information that appears
in "Certificate Details".
• The issuing location may not be displayed if you request 2 certificates at the same time. When you
install a certificate, be sure to check the certificate destination and installation procedure.
• Web Image Monitor can be used for creating the device certificate but not for requesting the
certificate to the certificate authority.
• Click [Cancel Request] to cancel the request for the device certificate.
Installing a Device Certificate (Issued by a Certificate Authority)
Install the device certificate using Web Image Monitor. For details about the displayed items and
selectable items, see Web Image Monitor Help.
This section explains the use of a certificate issued by a certificate authority as the device certificate.
Protecting Communication Paths via a Device Certificate
83
Содержание PRO C9100
Страница 2: ......
Страница 8: ...List of Operation Privileges for Address Books 229 INDEX 231 6...
Страница 24: ...1 Getting Started 22...
Страница 72: ...4 Preventing Leakage of Information from Machines 70...
Страница 116: ...5 Enhanced Network Security 114...
Страница 176: ...6 Managing the Machine 174...
Страница 188: ...7 Troubleshooting 186...
Страница 218: ...System Log Settings User Mach N W File Unset Set System Log R R R R R 8 List of Operation Privileges for Settings 216...
Страница 220: ...Settings User Mach N W File Unset Set Device Access Violation R W 8 List of Operation Privileges for Settings 218...
Страница 235: ......
Страница 236: ...EN GB EN US EN AU M238 1022 2014...