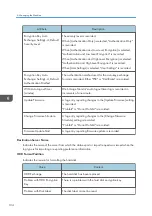
Value
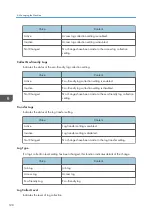
Content
0xffffff80
System operations
0xffffff81
System operations, Operations that were performed by non-
authenticated users
0xffffff86
Supervisor
0xffffff87
Administrator
0xffffff88
Administrator 1
0xffffff89
Administrator 2
0xffffff8a
Administrator 3
0xffffff8b
Administrator 4
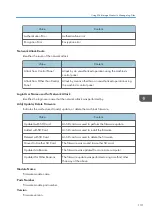
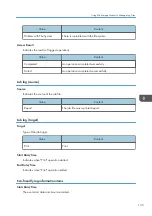
User Code/User Name
Identifies the user code or name of the user who performed the operation.
If an administrator performed the operation, his or her ID contains the login user name of the
administrator.
Log ID
Identifies the ID that is assigned to the log.
This is a hexadecimal ID that identifies the log.
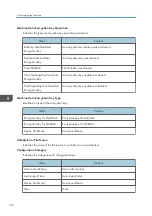
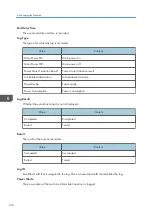
Access log information items
Access Log Type
Indicates the type of access.
Value
Content
Authentication
User authentication access
System
System access
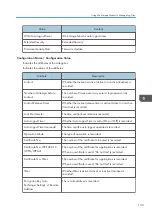
Network Attack Detection/
Encrypted Communication
Network attack or encrypted communication access
Firmware
Firmware verification access
Address Book
Address book access
6. Managing the Machine
124
Содержание PRO C9100
Страница 2: ......
Страница 8: ...List of Operation Privileges for Address Books 229 INDEX 231 6...
Страница 24: ...1 Getting Started 22...
Страница 72: ...4 Preventing Leakage of Information from Machines 70...
Страница 116: ...5 Enhanced Network Security 114...
Страница 176: ...6 Managing the Machine 174...
Страница 188: ...7 Troubleshooting 186...
Страница 218: ...System Log Settings User Mach N W File Unset Set System Log R R R R R 8 List of Operation Privileges for Settings 216...
Страница 220: ...Settings User Mach N W File Unset Set Device Access Violation R W 8 List of Operation Privileges for Settings 218...
Страница 235: ......
Страница 236: ...EN GB EN US EN AU M238 1022 2014...