• If the main power switch is turned off before "Erase All Memory" is completed, overwriting will be
stopped and data will be left on the hard disk.
• Do not stop the overwrite mid-process. Doing so will damage the hard disk.
• We recommend that before you erase the hard disk, you use Device Manager NX to back up the
Address Book. The Address Book can also be backed up using Web Image Monitor. For details,
see Device Manager NX Help or Web Image Monitor Help.
• The only operation possible during the "Erase All Memory" process is pausing. If "Random
Numbers" is selected and overwrite 3 times is set, the "Erase All Memory" process takes up to 4
hours and 45 minutes.
• The "Erase All Memory" function also clears the machine's security settings, so that neither machine
nor user administration will be possible. Ensure that users do not save any data on the machine
after "Erase All Memory" has completed.
Types of data that can be overwritten by Erase All Memory
• Information registered in the Address Book
• Counters stored under each user code
• Applications using Embedded Software Architecture
System Settings or other settings related to the device are initialized.
Methods of erasing
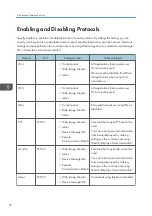
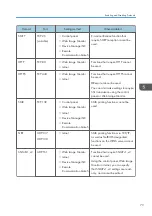
You can select a method of erasing from the following:
• NSA
Data is overwritten twice with random numbers and once with zeros.
• DoD
Data is overwritten by a random number, then by its complement, then by another random number,
and is then verified.
• Random Numbers
Data is overwritten multiple times with random numbers. The number of overwrites can be selected
from 1 to 9.
• BSI/VSITR
Data is overwritten 7 times with the following patterns: 0x00, 0xFF, 0x00, 0xFF, 0x00, 0xFF,
0xAA.
• Secure Erase
Data is overwritten using an algorithm that is built in to the hard disk drive.
Deleting Data on the Machine
67
Содержание PRO C9100
Страница 2: ......
Страница 8: ...List of Operation Privileges for Address Books 229 INDEX 231 6...
Страница 24: ...1 Getting Started 22...
Страница 72: ...4 Preventing Leakage of Information from Machines 70...
Страница 116: ...5 Enhanced Network Security 114...
Страница 176: ...6 Managing the Machine 174...
Страница 188: ...7 Troubleshooting 186...
Страница 218: ...System Log Settings User Mach N W File Unset Set System Log R R R R R 8 List of Operation Privileges for Settings 216...
Страница 220: ...Settings User Mach N W File Unset Set Device Access Violation R W 8 List of Operation Privileges for Settings 218...
Страница 235: ......
Страница 236: ...EN GB EN US EN AU M238 1022 2014...