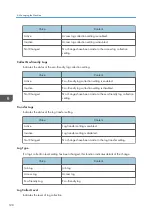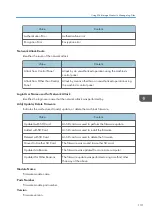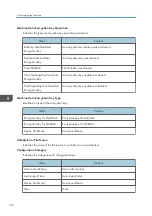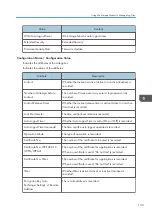
If "Eco-friendly Log Collect Level" is set to [Level 2], all eco-friendly logs are collected.
1.
Log in as the machine administrator from Web Image Monitor.
2.
Point to [Device Management], and then click [Configuration].
3.
Click [Logs] under "Device Settings".
4.
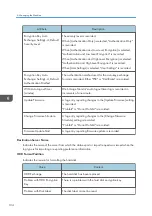
Select [Active] for each function: "Collect Job Logs", "Collect Access Logs" and "Collect
Eco-friendly Logs".
5.
Specify the collection level for each function, "Job Log Collect Level", "Access Log Collect
Level", and "Eco-friendly Log Collect Level".
When a level is changed, the selection status of log details changes according to the level.
To change individual items of the log details, configure the setting for each item. Even if the
collection level is set to [Level 1] or [Level 2], once each item of the log details is changed, the level
changes to [User Settings].
6.
Click [OK].
7.
"Updating..." appears. Wait for about 1 or 2 minutes, and then click [OK].
If the previous screen does not appear again after you click [OK], wait for a while, and then click
the web browser's refresh button.
8.
Log out.
• The greater "Access Log Collect Level" setting value, the more logs are collected.
Downloading Logs
Use the following procedure to convert the logs stored in the machine into a CSV file for simultaneous
batch download.
To collect logs, configure the collection setting for job log, access log and eco-friendly log to [Active].
This setting can be specified in [Logs] under [Configuration] in Web Image Monitor.
1.
Log in as the machine administrator from Web Image Monitor.
2.
Point to [Device Management], and then click [Configuration].
3.
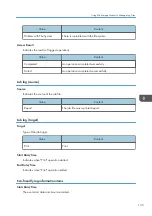
Click [Download Logs] under "Device Settings".
4.
Select the type of log to download from the drop-down box in "Logs to Download".
The security log includes 2 kinds of logs: job log and access log.
5.
Click [Download].
6.
Specify the folder in which you want to save the file.
7.
Click [Back].
Using Web Image Monitor to Manage Log Files
139
Содержание PRO C9100
Страница 2: ......
Страница 8: ...List of Operation Privileges for Address Books 229 INDEX 231 6...
Страница 24: ...1 Getting Started 22...
Страница 72: ...4 Preventing Leakage of Information from Machines 70...
Страница 116: ...5 Enhanced Network Security 114...
Страница 176: ...6 Managing the Machine 174...
Страница 188: ...7 Troubleshooting 186...
Страница 218: ...System Log Settings User Mach N W File Unset Set System Log R R R R R 8 List of Operation Privileges for Settings 216...
Страница 220: ...Settings User Mach N W File Unset Set Device Access Violation R W 8 List of Operation Privileges for Settings 218...
Страница 235: ......
Страница 236: ...EN GB EN US EN AU M238 1022 2014...