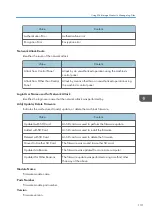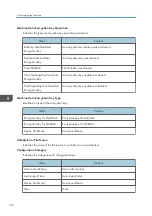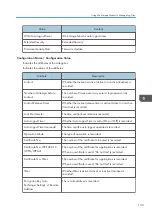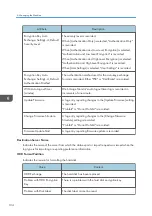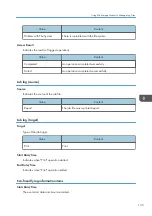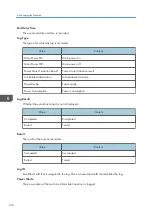
1. Access log
2. Job log
3. Download
4. Downloaded logs
5. Overwriting
6. Deleted by overwriting
Check the message in the last line of the downloaded logs to determine whether or not overwriting
occurred while the logs were downloading,
• If overwriting did not occur, the last line will contain the following message: Download
completed.
• If overwriting did occur, the last line will contain the following message: Download
completed. A part of the logs before Log ID xxxx does not exist any more.
• If overwriting occurs, part of the logs will be deleted by the overwriting, so check the log "Log ID
xxxx" and more recent logs.
Deleting All Logs
Use the following procedure to delete all logs stored on the machine.
"Delete All Logs" appears if one of the job log, access log, or eco-friendly log is set to [Active].
1.
Log in as the machine administrator from Web Image Monitor.
2.
Point to [Device Management], and then click [Configuration].
3.
Click [Logs] under "Device Settings".
4.
Click [Delete] under "Delete All Logs".
5.
Click [OK].
6.
Log out.
Disabling Log Transfer to the Log Collection Server
Use the following procedure to disable log transfer to the log collection server. Note that you can switch
the log transfer setting to [Inactive] only if it is already set to [Active].
1.
Log in as the machine administrator from Web Image Monitor.
2.
Point to [Device Management], and then click [Configuration].
3.
Click [Logs] under "Device Settings".
Using Web Image Monitor to Manage Log Files
143
Содержание PRO C9100
Страница 2: ......
Страница 8: ...List of Operation Privileges for Address Books 229 INDEX 231 6...
Страница 24: ...1 Getting Started 22...
Страница 72: ...4 Preventing Leakage of Information from Machines 70...
Страница 116: ...5 Enhanced Network Security 114...
Страница 176: ...6 Managing the Machine 174...
Страница 188: ...7 Troubleshooting 186...
Страница 218: ...System Log Settings User Mach N W File Unset Set System Log R R R R R 8 List of Operation Privileges for Settings 216...
Страница 220: ...Settings User Mach N W File Unset Set Device Access Violation R W 8 List of Operation Privileges for Settings 218...
Страница 235: ......
Страница 236: ...EN GB EN US EN AU M238 1022 2014...