LTE CPE B2368 User's
Guide
5 Wireless WiFi 2.4 / 5 GHz
Issue 01
Copyright © Huawei Technologies Co., Ltd.
51
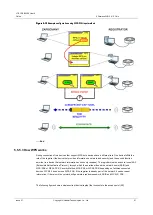
Figure 5-12
Example configuration using WPS PIN input method
Figure 5-12
Example configuration using WPS PIN input method
---- End
5.5.5.3 How WPS works
During connection of two devices that support WPS both devices have a different role. One device fulfills the
role of the registrar (the device that provides information on network and security) and the second function
enrollee (ie a device that network information and security receives). The registrar creates a secure tunnel EAP
(Extensible Authentication Protocol), through which the enrollee will send the network name (SSID) and
WPA-PSK or WPA2-PSK. Security Method, WPA-PSK or WPA2-PSK, depending on facilities connected
devices. WPS 2.0 does not use WPA-PSK. If the registrar is already part of the network, it sends current
information. If there is still no network, will generate a random password, SSID and WPA (2) PSK.
The following figure shows a wireless client device (laptop) that connects to the access point (AP).