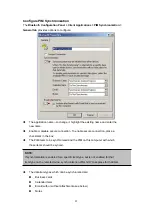
Chapter 8
Security
8.1 AUTHENTICATION
Authentication is used to verify identity; it requires a passkey or link key from the remote
device. When a remote device attempts access, a visual and/or audio warning notifies the
local operator.
If the notification is ignored, access is denied after a preset timeout.
When devices are “paired,” those devices automatically exchange a Link Key and
Authentication is carried out without operator intervention.
8.2 AUTHORIZATION
Authorization is Yes-or-No security that requires operator intervention to avoid having
the connection time out and fail.
Authorization is limited to:
Yes
, you may connect (click the balloon to proceed)
No
, you may not connect (ignore the balloon prompt and the connection will
fail).
8.3 ENCRYPTION
Encrypting data translates it into an unreadable format using a secret key or password.
Decrypting the data requires the same key or password that was used to encrypt it.
8.4 LINK KEY
A unique, internally generated, access code based on a passkey, the Bluetooth Device
Address and an internally generated random number. Link Keys are generated
automatically when devices Pair.
After a link key is generated, manual entry of the passkey is not required.
8.5 PAIRING DEVICES
Pairing allows you to avoid entering access information each time a connection is
attempted. Paired devices share a unique Link Key, which they exchange each time they
91
Содержание BF-8000
Страница 1: ...Wireless Bluetooth USB Dongle User s Guide 1...
Страница 26: ...Figure 4 Device Icons for Windows XPDevice Ions for Windows Figure 5 Service Icons for Windows XP 26...
Страница 27: ...NOTE Services may be unavailable because they are in use or because the necessary hardware is not installed 27...
Страница 63: ...Click Next to find the printer Select the Bluetooth server select the shared printer and click Next 63...