A V G 9 I nternet Sec urity © 2 0 1 0 C opyright A V G T ec hnologies C Z, s .r.o. A ll rights res erved.
5 3
not display dialogs asking you whether you want to allow or block
communication for unknown applications. In case an unknown application tries
to communicate over the network at that time, the
Firewall
will allow or block
the attempt automatically according to settings in the current profile.
·
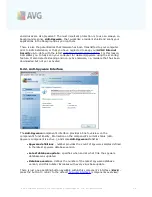
Firewall status
:
o
Firewall enabled
- select this option to allow communication to those
applications that are assigned as 'allowed' in the set of rules defined
within selected
Firewall
profile
o
Firewall disabled
- this option switches
Firewall
off completely, all
network traffic is allowed but not checked!
o
Emergency mode (block all internet traffic)
- select this option to
block all traffic on every single network port;
Firewall
is still running but
all network traffic is stopped
Please note:
The software vendor has set up all AVG components to give optimum
performance. Unless you have a real reason to do so, do not change the AVG
configuration. Any changes to settings should only be performed by an experienced
user. If you need to change Firewall configuration, select the system menu item
Tools/Firewall settings
and edit the Firewall configuration in the newly opened
Firewall Settings
dialog.
Control buttons
·
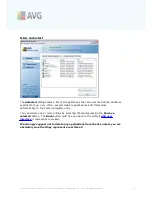
Configuration wizard
- press the button to switch to the respective dialog (
used within installation process
) called
Computer Usage Selection
where you
can specify the
Firewall
component configuration
·
Save changes
- press this button to save and apply any changes made in this
dialog
·
Cancel
- press this button to return to the default
AVG user interface
(
components overview
)
8.8. E-mail Scanner
One of the most common sources of viruses and trojans is via e-mail. Phishing and
spam make e-mail an even greater source of risks. Free e-mail accounts are more likely
to receive such malicious e-mails (
as they rarely employ anti-spam technology
), and
home users rely quite heavily on such e-mail. Also home users, surfing unknown sites
and filling in online forms with personal data (
such as their e-mail address
) increase
exposure to attacks via e-mail. Companies usually use corporate e-mail accounts and
employ anti-spam filters etc, to reduce the risk.