A V G 9 I nternet Sec urity © 2 0 1 0 C opyright A V G T ec hnologies C Z, s .r.o. A ll rights res erved.
5 7
The control buttons available within the
E-mail Scanner detection
interface are as
follows:
·
Refresh list
- updates the list of detected threats
·
Back
- switches you back to the previously displayed dialog
8.9. ID Protection
AVG Identity Protection
is an anti-malware product that is focused on preventing
identity thieves from stealing your passwords, bank account details, credit card
numbers and other personal digital valuables from all kinds of malicious software (
malware
) that target your PC. It makes sure that all programs running on your PC are
operating correctly.
AVG Identity Protection
spots and blocks suspicious behavior on
a continuous basis and protects your computer from all new malware.
8.9.1. ID Protection Principles
AVG Identity Protection
is an anti-malware component that protects you from all
kinds of malware (
spyware, bots, identity theft, ...
) using behavioral technologies and
provide zero day protection for new viruses. As malware gets sophisticated and comes
in a form of normal programs that can open up your PC to the remote attacker for
identity theft,
AVG Identity Protection
secures you from these new execution based
malware. It is a complimentary protection to
AVG Anti-Virus
that protects you from
file based and known viruses using signature mechanism and scanning.
We strongly recommend you have the both
AVG Anti-Virus
and AVG Identity
Protection components installed, in order to have complete protection for your
PC.
8.9.2. ID Protection Interface
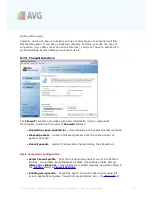
The
Identity Protection
component interface provides a brief description of the
component's basic functionality, its status (
AVG Identity Protection is active and fully
functional.
) and some statistical data:
·
Malware items removed
- gives the number of applications detected as
malware, and removed
·
Processes monitored
- number of currently running applications that are
being monitored by IDP
·
Behaviors monitored
- number of specific actions running within the
monitored applications