A V G 9 I nternet Sec urity © 2 0 1 0 C opyright A V G T ec hnologies C Z, s .r.o. A ll rights res erved.
1 6 1
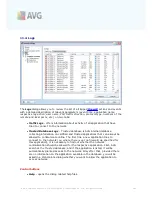
11.4. Logs
The
Logs
dialog allows you to review the list of all logged
Firewall
actions and events
with a detailed description of relevant parameters (
event time, application name,
respective log action, user name, PID, traffic direction, protocol type, numbers of the
remote and local ports, etc.
) on two tabs:
·
Traffic Logs
- offers information about activity of all application that have
tried to connect to the network.
·
Trusted Database Logs
-
Trusted database
is AVG internal database
collecting information on certified and trusted applications that can always be
allowed to communicate online. The first time a new application tries to
connect to the network (
i.e. where there is yet no firewall rule specified for
this application
), it is necessary to find out whether the network
communication should be allowed for the respective application. First, AVG
searches the
Trusted database
, and if the application is listed, it will be
automatically granted access to the network. Only after that, provided there
are no information on the application available in the database, you will be
asked in a stand-alone dialog whether you want to allow the application to
access network.
Control buttons
·
Help
- opens the dialog related help files.