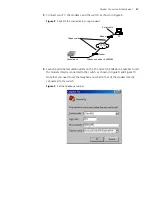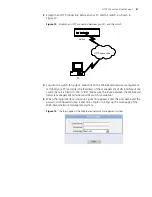
7
C
ONTROLLING
L
OGIN
U
SERS
Introduction
A switch provides ways to control different types of login users, as listed in Table 24.
Controlling Telnet
Users
Prerequisites
The controlling policy against Telnet users is determined, including the source and
destination IP addresses to be controlled and the controlling actions (permitting or
denying).
Controlling Telnet Users
by Source IP Addresses
Controlling Telnet users by source IP addresses is achieved by applying basic ACLs,
which are numbered from 2000 to 2999.
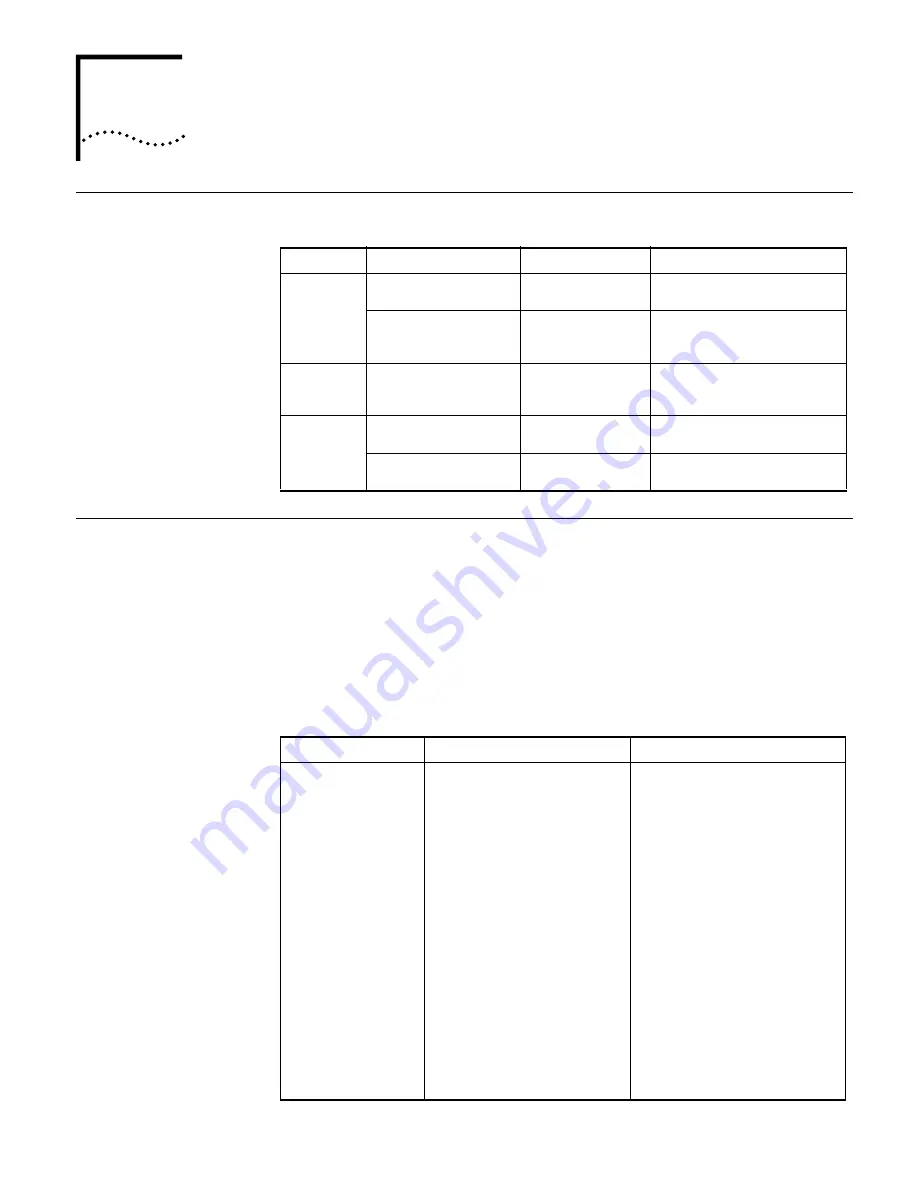
Table 24
Ways to control different types of login users
Login mode Control method
Implementation
Related section
Telnet
By source IP addresses
Through basic ACLs
Controlling Telnet Users by
Source IP Addresses
By source and
destination IP addresses
Through advanced
ACLs
Controlling Telnet Users by
Source and Destination IP
Addresses
SNMP
By source IP addresses
Through basic ACLs
Controlling Network
Management Users by Source IP
Addresses
WEB
By source IP addresses
Through basic ACLs
Controlling Web Users by
Source IP Address.
Disconnect Web users by
force
By executing
commands in CLI
Disconnecting a Web User by
Force.
Table 25
Control Telnet users by source IP addresses
Operation
Command
Description
Enter system view
system-view
Create a basic ACL or
enter basic ACL view
acl number
acl-number
[
match-order
{
config
|
auto
} ]
As for the
acl number
command,
the
config
keyword is specified by
default.
Define rules for the
ACL
rule
[
rule-id
] {
permit
|
deny
} [
source
{
sour-addr sour-wildcard
|
any
} ] [
time-range
time-name ]
[
fragment
]
Required
Quit to system view
quit
Enter user interface
view
user-interface
[
type
]
first-number
[
last-number
]
Apply the ACL to
control Telnet users by
source IP addresses
acl
acl-number
{
inbound
|
outbound
}
Required
The
inbound
keyword specifies to
filter the users trying to Telnet to
the current switch.
The
outbound
keyword specifies
to filter users trying to Telnet to
other switches from the current
switch.
Содержание 4200G 12-Port
Страница 10: ...8 CONTENTS...
Страница 14: ...4 ABOUT THIS GUIDE...
Страница 46: ...32 CHAPTER 5 LOGGING IN THROUGH WEB BASED NETWORK MANAGEMENT SYSTEM...
Страница 48: ...34 CHAPTER 6 LOGGING IN THROUGH NMS...
Страница 60: ...46 CHAPTER 9 VLAN CONFIGURATION...
Страница 64: ...50 CHAPTER 10 MANAGEMENT VLAN CONFIGURATION...
Страница 80: ...66 CHAPTER 13 GVRP CONFIGURATION...
Страница 98: ...84 CHAPTER 15 LINK AGGREGATION CONFIGURATION...
Страница 112: ...98 CHAPTER 18 MAC ADDRESS TABLE MANAGEMENT...
Страница 126: ...112 CHAPTER 19 LOGGING IN THROUGH TELNET...
Страница 162: ...148 CHAPTER 20 MSTP CONFIGURATION...
Страница 274: ...260 CHAPTER 29 IGMP SNOOPING CONFIGURATION...
Страница 276: ...262 CHAPTER 30 ROUTING PORT JOIN TO MULTICAST GROUP CONFIGURATION...
Страница 298: ...284 CHAPTER 33 SNMP CONFIGURATION...
Страница 304: ...290 CHAPTER 34 RMON CONFIGURATION...
Страница 338: ...324 CHAPTER 36 SSH TERMINAL SERVICES...
Страница 356: ...342 CHAPTER 38 FTP AND TFTP CONFIGURATION...
Страница 365: ...Information Center Configuration Example 351 S4200G terminal logging...
Страница 366: ...352 CHAPTER 39 INFORMATION CENTER...
Страница 378: ...364 CHAPTER 40 BOOTROM AND HOST SOFTWARE LOADING...
Страница 384: ...370 CHAPTER 41 Basic System Configuration and Debugging...
Страница 388: ...374 CHAPTER 43 NETWORK CONNECTIVITY TEST...
Страница 406: ...392 CHAPTER 45 CONFIGURATION OF NEWLY ADDED CLUSTER FUNCTIONS...
Страница 422: ...408 CHAPTER 48 UDP HELPER CONFIGURATION...