208
C
HAPTER
26: ACL C
ONFIGURATION
Configuration Tasks
In the case that you specify the rule ID when defining a rule:
■
If the rule corresponding to the specified rule ID already exists, you will edit the
rule, and the modified part in the rule will replace the original content, while other
parts remain unchanged.
■
If the rule corresponding to the specified rule ID does not exists, you will create
and define a new rule.
■
The content of a modified or created rule must not be identical with the content
of any existing rule; otherwise the rule modification or creation will fail, and the
system will prompt that the rule already exists.
If you do not specify a rule ID, you will create and define a new rule, and the system
will assign an ID for the rule automatically.
rule-string
: rule information, which can be combination of the parameters given in
Table 180. Table 180 describes the specific parameters.
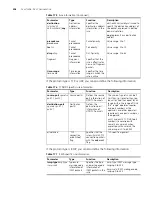
Table 179
Configure a Layer 2 ACL rule
Operation
Command
Description
Enter system view
system-view
-
Create or enter layer
2 ACL view
acl number
acl-number
[
match-order
{
config
|
auto
} ]
By the default, the match order is
config
Define an rule
rule
[
rule-id
] {
permit
|
deny }
rule-string
Required
Define the comment
string of the ACL rule
rule
rule-id
comment
text
Optional
Define the description
information of the
ACL
description
text
Optional
Display ACL
information
display
acl
{
all
|
acl-number
}
Optional
The
display
command can be
executed in any view
Table 180
Rule information
Parameter
Type
Function
Description
format-type
Link layer
encapsulation
type
Defines the link
layer
encapsulation
type in the rule
format-type
: the value can be
802.3/802.2, 802.3, ether_ii, or snap
lsap
lsap-code
lsap-wildcard
lsap field
Defines the lsap
field in the rule
lsap-code
: the encapsulation format
of data frames, a 16-bit hexadecimal
number
lsap-wildcard
: mask of the lsap value,
a 16-bit hexadecimal number used to
specify the mask bit
source
{
source-addr
source-mask
|
vlan-id
}*
Source MAC
address
information
Specifies the
source MAC
address range in
the rule
source-addr
: source MAC address, in
the format of H-H-H
source- mask
: source MAC address
mask, in the format of H-H-H
vlan-id
: source VLAN ID, in the range
of 1 to 4,094
dest
dest-addr
dest-mask
Destination MAC
address
information
Specifies the
destination MAC
address range in
the rule
dest-addr
: destination MAC address,
in the format of H-H-H
dest- mask
: destination MAC address
mask, in the format of H-H-H
Содержание 4200G 12-Port
Страница 10: ...8 CONTENTS...
Страница 14: ...4 ABOUT THIS GUIDE...
Страница 46: ...32 CHAPTER 5 LOGGING IN THROUGH WEB BASED NETWORK MANAGEMENT SYSTEM...
Страница 48: ...34 CHAPTER 6 LOGGING IN THROUGH NMS...
Страница 60: ...46 CHAPTER 9 VLAN CONFIGURATION...
Страница 64: ...50 CHAPTER 10 MANAGEMENT VLAN CONFIGURATION...
Страница 80: ...66 CHAPTER 13 GVRP CONFIGURATION...
Страница 98: ...84 CHAPTER 15 LINK AGGREGATION CONFIGURATION...
Страница 112: ...98 CHAPTER 18 MAC ADDRESS TABLE MANAGEMENT...
Страница 126: ...112 CHAPTER 19 LOGGING IN THROUGH TELNET...
Страница 162: ...148 CHAPTER 20 MSTP CONFIGURATION...
Страница 274: ...260 CHAPTER 29 IGMP SNOOPING CONFIGURATION...
Страница 276: ...262 CHAPTER 30 ROUTING PORT JOIN TO MULTICAST GROUP CONFIGURATION...
Страница 298: ...284 CHAPTER 33 SNMP CONFIGURATION...
Страница 304: ...290 CHAPTER 34 RMON CONFIGURATION...
Страница 338: ...324 CHAPTER 36 SSH TERMINAL SERVICES...
Страница 356: ...342 CHAPTER 38 FTP AND TFTP CONFIGURATION...
Страница 365: ...Information Center Configuration Example 351 S4200G terminal logging...
Страница 366: ...352 CHAPTER 39 INFORMATION CENTER...
Страница 378: ...364 CHAPTER 40 BOOTROM AND HOST SOFTWARE LOADING...
Страница 384: ...370 CHAPTER 41 Basic System Configuration and Debugging...
Страница 388: ...374 CHAPTER 43 NETWORK CONNECTIVITY TEST...
Страница 406: ...392 CHAPTER 45 CONFIGURATION OF NEWLY ADDED CLUSTER FUNCTIONS...
Страница 422: ...408 CHAPTER 48 UDP HELPER CONFIGURATION...