Chapter 7 Wireless LAN
P-2812HNU-51c User’s Guide
151
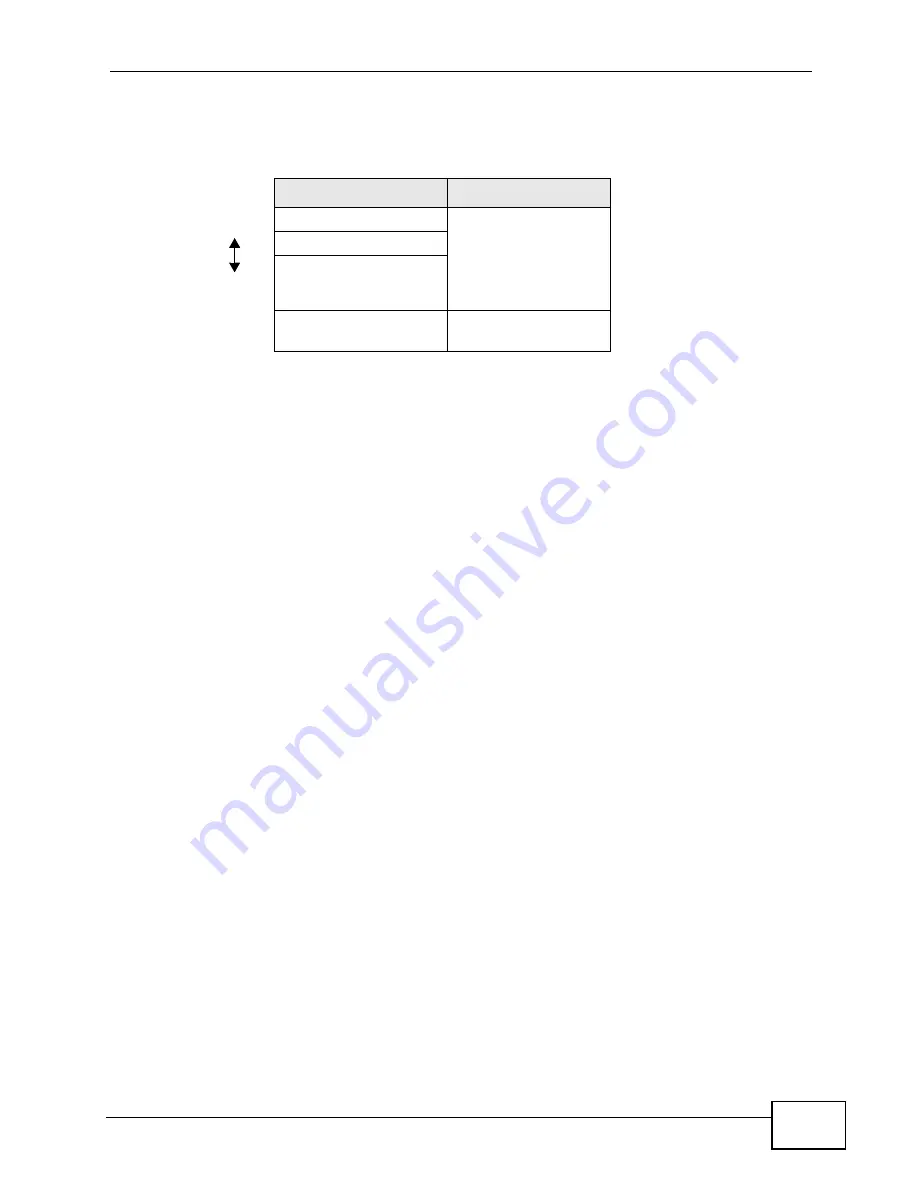
The types of encryption you can choose depend on the type of authentication.
(See
for information about this.)
For example, if the wireless network has a RADIUS server, you can choose WPA
or WPA2. If users do not log in to the wireless network, you can choose no
encryption, Static WEP, WPA-PSK, or WPA2-PSK.
Usually, you should set up the strongest encryption that every device in the
wireless network supports. For example, suppose you have a wireless network
with the P-2812HNU-51c and you do not have a RADIUS server. Therefore, there
is no authentication. Suppose the wireless network has two devices. Device A only
supports WEP, and device B supports WEP and WPA. Therefore, you should set up
Static WEP in the wireless network.
Note: It is recommended that wireless networks use
WPA-PSK
,
WPA
, or stronger
encryption. The other types of encryption are better than none at all, but it is still
possible for unauthorized wireless devices to figure out the original information
pretty quickly.
When you select WPA2 or WPA2-PSK in your P-2812HNU-51c, you can also
select an option (WPA compatible) to support WPA as well. In this case, if some
of the devices support WPA and some support WPA2, you should set up WPA2-
PSK or WPA2 (depending on the type of wireless network login) and select the
WPA compatible option in the P-2812HNU-51c.
Many types of encryption use a key to protect the information in the wireless
network. The longer the key, the stronger the encryption. Every device in the
wireless network must have the same key.
7.10.4 WiFi Protected Setup
Your P-2812HNU-51c supports WiFi Protected Setup (WPS), which is an easy way
to set up a secure wireless network. WPS is an industry standard specification,
defined by the WiFi Alliance.
WPS allows you to quickly set up a wireless network with strong security, without
having to configure security settings manually. Each WPS connection works
Table 41
Types of Encryption for Each Type of Authentication
NO AUTHENTICATION RADIUS SERVER
Weakest
No Security
WPA
Static WEP
WPA-PSK
Stronges
t
WPA2-PSK
WPA2
Summary of Contents for P-2812HNU-51c
Page 2: ......
Page 8: ...Safety Warnings P 2812HNU 51c User s Guide 8 ...
Page 10: ...Contents Overview P 2812HNU 51c User s Guide 10 ...
Page 19: ...19 PART I User s Guide ...
Page 20: ...20 ...
Page 73: ...73 PART II Technical Reference ...
Page 74: ...74 ...
Page 88: ...Chapter 4 Status Screens P 2812HNU 51c User s Guide 88 ...
Page 118: ...Chapter 5 WAN Setup P 2812HNU 51c User s Guide 118 ...
Page 204: ...Chapter 9 Voice P 2812HNU 51c User s Guide 204 ...
Page 210: ...Chapter 10 File Sharing P 2812HNU 51c User s Guide 210 ...
Page 216: ...Chapter 11 Firewall P 2812HNU 51c User s Guide 216 ...
Page 223: ...Chapter 12 Certificate P 2812HNU 51c User s Guide 223 Figure 99 Certificate Details ...
Page 232: ...Chapter 13 Static Route P 2812HNU 51c User s Guide 232 ...
Page 236: ...Chapter 14 Policy Forwarding P 2812HNU 51c User s Guide 236 ...
Page 252: ...Chapter 16 Quality of Service QoS P 2812HNU 51c User s Guide 252 ...
Page 274: ...Chapter 19 Universal Plug and Play UPnP P 2812HNU 51c User s Guide 274 ...
Page 284: ...Chapter 21 Interface Group P 2812HNU 51c User s Guide 284 ...
Page 288: ...Chapter 22 System Settings P 2812HNU 51c User s Guide 288 ...
Page 292: ...Chapter 23 Logs P 2812HNU 51c User s Guide 292 ...
Page 300: ...Chapter 24 Tools P 2812HNU 51c User s Guide 300 ...
Page 320: ...Chapter 27 Product Specifications P 2812HNU 51c User s Guide 320 ...
Page 336: ...Appendix A Network Troubleshooting P 2812HNU 51c User s Guide 336 ...
Page 376: ...Appendix C Pop up Windows JavaScripts and Java Permissions P 2812HNU 51c User s Guide 376 ...
Page 388: ...Appendix D IP Addresses and Subnetting P 2812HNU 51c User s Guide 388 ...






























