UTT Technologies
Chapter 10 VPN
http://www.uttglobal.com
Page
13513513
2
AutoKey (IKE)
Bidirectional (Gateway-to-Gateway IPSec VPN)
Main Mode
3
AutoKey (IKE)
Originate-Only (Dynamic-to-Static IPSec VPN)
Aggressive Mode
4
AutoKey (IKE)
Answer-Only (Static-to-Dynamic IPSec VPN)
Aggressive Mode
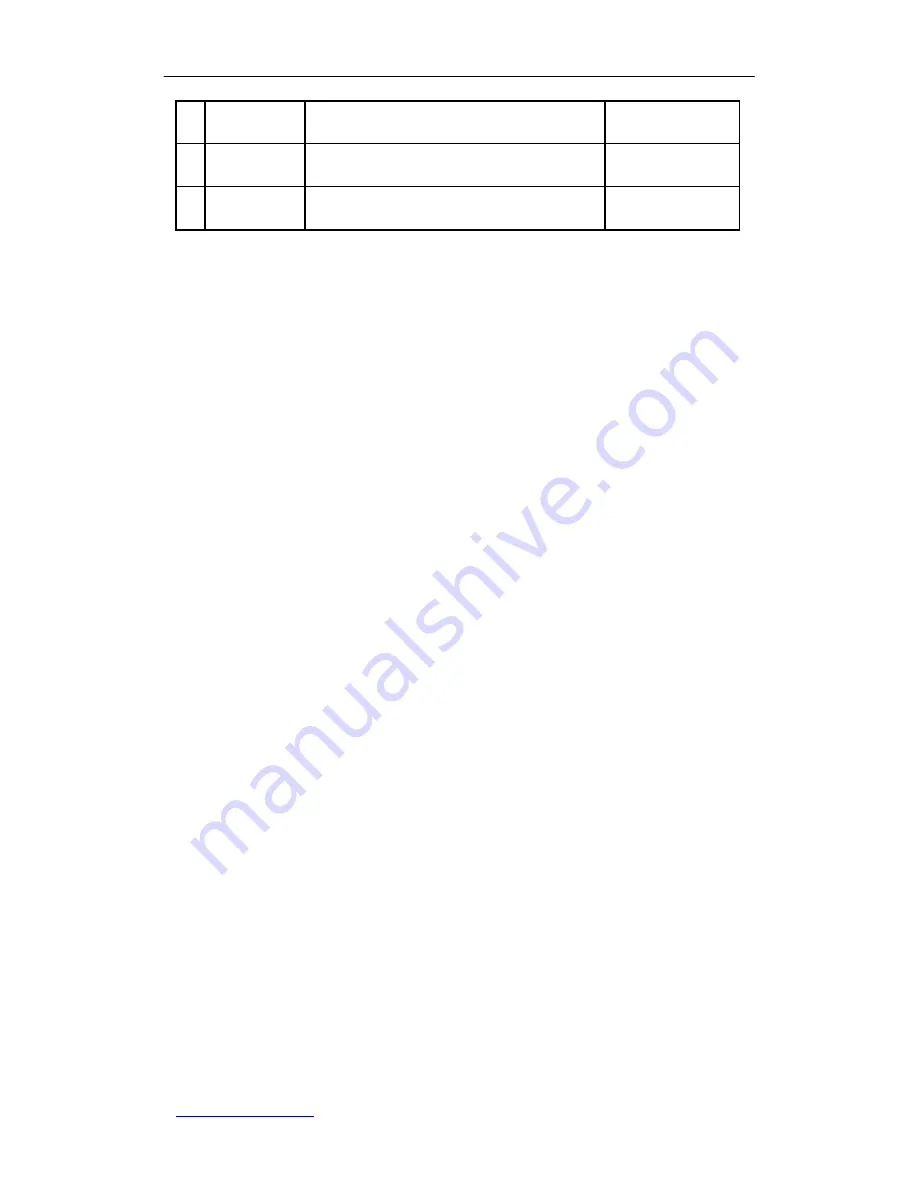
Table 11-1 Four Types of IPSec VPN Configuration
In the first and second types of IPSec VPN configuration, both IPSec endpoints have
static IP addresses; in the third type, the local UTT VPN gateway has a dynamic IP
address, while the remote endpoint (another UTT VPN gateway or compatible VPN
appliance) has a static IP address; and in the last type, the local UTT VPN gateway has a
static IP address, while the remote endpoint (another UTT VPN gateway or compatible
VPN appliance) has a dynamic IP address. In addition, on the local UTT VPN gateway,
you can specify a Fully Qualified Domain Name (FQDN) instead of an IP address for the
remote IPSec endpoint (another UTT VPN gateway or compatible VPN appliance that
supports DDNS) with a dynamic IP address; this means that you can establish an IPSec
tunnel between two endpoints that both have dynamic IP addresses.
9.5.1.1
Concepts and Protocols
In order for the IPSec tunnel to be established and function properly, the two IPSec
endpoints must agree on the SAs. The IPSec SAs determine a number of security
parameters (like security protocol, security algorithms and keys, SA lifetime, etc.)
necessary to secure and maintain the IPSec tunnel effectively. An SA is uniquely identified
by three parameters: security parameters index (SPI), destination IP address, and
security protocol (AH or ESP).
Through the SAs, an IPSec tunnel can provide any combination of the following types of
protection:
•
Data Confidentiality:
The IPSec sender can encrypt datagrams before transmitting
them, and only the IPSec receiver can decrypt and read them.
•
Data Integrity:
The IPSec receiver can verify that the datagram is not altered during
transmission, either deliberately or due to random errors.
•
Data Origin Authentication:
The IPSec receiver can verify that each datagram is
originated by the claimed sender.
•
Anti-Replay
: The IPSec receiver can detect and reject replayed packets (i.e., old or
duplicate packets) to prevent replay attacks.
IPSec provides two security protocols including AH and ESP for protecting data. AH is
used to provide data authentication service (data origin authentication and data integrity).
















































