Chapter 1
Introduction
RUGGEDCOM ROS
User Guide
26
SSH and SSL Keys and Certificates
• 2 indicates the corresponding status for the device to be false
Reading the FailSafe Relay Status From a Device Using TruthValue
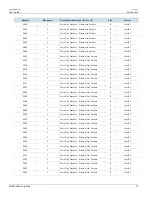
To understand how to use the TruthValue format to read the FailSafe Relay status from a device, consider a
ModBus request to read multiple registers from location 0x0044.
0x04
0x00
0x44
0x00
0x01
The response may look like:
0x04
0x02
0x00
0x01
The register's lower byte shows the FailSafe Relay status. In this example, the FailSafe Relay is energized.
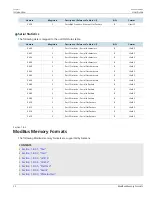
Reading the ErrorAlarm Status From a Device Using TruthValue
To understand how to use the TruthValue format to read the ErrorAlarm status from a device, conside a ModBus
request to read mulitple registers from location 0x0045.
0x04
0x00
0x45
0x00
0x01
The response may look like:
0x04
0x02
0x00
0x01
The register's lower byte shows the ErrorAlarm status. In this example, there is no active ERROR, ALERT or CRITICAL
alarm in the device.
Section 1.9
SSH and SSL Keys and Certificates
The following describes the SSH and SSL keys and certificates in RS900, along with the certificate and SSH key
requirements.
CONTENTS
•
Section 1.9.1, “Certificate and Keys Life Cycle”
•
Section 1.9.2, “Certificate and Key Requirements”
Section 1.9.1
Certificate and Keys Life Cycle
Each RUGGEDCOM ROS device is shipped with an SSL certificate and RSA key pair, and a DSA host key pair for
SSH, that are generated at and provisioned by the factory. The administrator may upload a new certificate and
keys to the system at any time, which will overwrite the existing ones. In addition, CLI commands are available to
regenerate SSL certificate and key pair as well as the SSH host key pair.
There are three types of certificates and keys used in RUGGEDCOM ROS: