Enterprise Multi-WAN VPN QoS Router
109
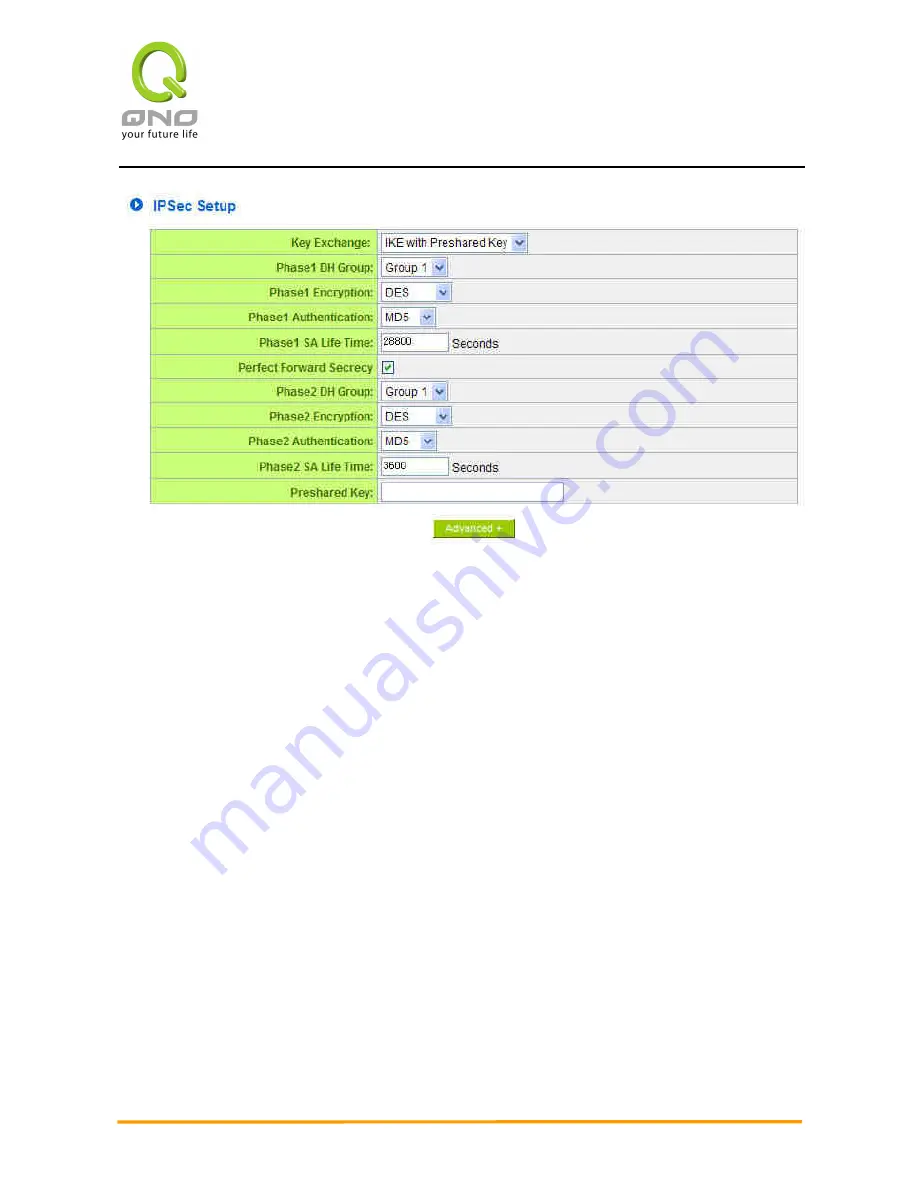
Use IKE Protocol
:
Click the shared key generated by IKE to encrypt and authenticate the remote user. If
PFS (Perfect Forward Secrecy) is enabled, the Phase 2 shared key generated during the IKE
coordination will conduct further encryption and authentication. When PFS is enabled,
hackers using brute force to capture the key will not be able to get the Phase 2 key in such
a short period of time.
Perfect Forward Secrecy:
When users check the PFS option, don't forget to
activate the PFS function of the VPN device and the VPN Client as well.
Phase 1/ Phase 2 DH Group:
This option allows users to select Diffie-Hellman
groups: Group 1/ Group 2/ Group 5.
Phase 1/ Phase 2 Encryption:
This option allows users to set this VPN tunnel to
use any encryption mode. Note that this parameter must be identical to that of the
remote encryption parameter: DES (64-bit encryption mode), 3DES (128-bit
encryption mode), AES (the standard of using security code to encrypt information).
It supports 128-bit, 192-bit, and 256-bit encryption keys.
Phase 1/Phase 2 Authentication:
This authentication option allows users to set
this VPN tunnel to use any authentication mode. Note that this parameter must be
















































