VigorPro5510 Series User’s Guide
235
3
3
.
.
1
1
7
7
D
D
i
i
a
a
g
g
n
n
o
o
s
s
t
t
i
i
c
c
s
s
Diagnostic Tools provide a useful way to
view
or
diagnose
the status of your Vigor router.
Below shows the menu items for Diagnostics.
3
3
.
.
1
1
7
7
.
.
1
1
D
D
i
i
a
a
l
l
-
-
o
o
u
u
t
t
T
T
r
r
i
i
g
g
g
g
e
e
r
r
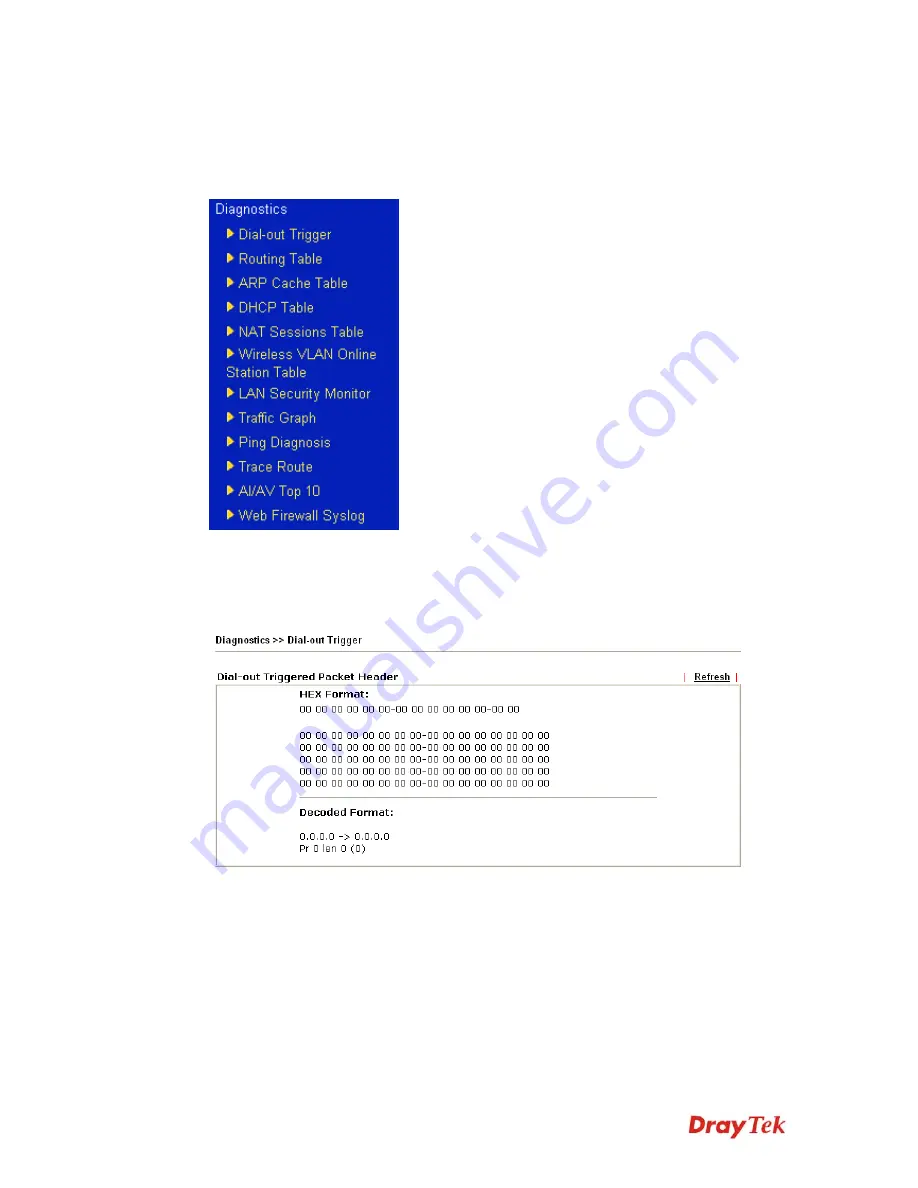
Click
Diagnostics
and click
Dial-out Trigger
to open the web page. The internet connection
(e.g., ISDN, PPPoE, PPPoA, etc) is triggered by a package sending from the source IP
address.
Decoded Format
It shows the source IP address (local), destination IP (remote)
address, the protocol and length of the package.
Refresh
Click it to reload the page.
Summary of Contents for VigorPro 5510 Series
Page 1: ......
Page 3: ...VigorPro5510 Series User s Guide iii ...
Page 10: ......
Page 22: ...VigorPro5510 Series User s Guide 12 This page is left blank ...
Page 38: ...VigorPro5510 Series User s Guide 28 ...
Page 131: ...VigorPro5510 Series User s Guide 121 ...
Page 301: ...VigorPro5510 Series User s Guide 291 10 Click Send Now the firmware update is finished ...






























